Data Broker Opt-Outs for CEO Fraud Prevention
Table of Contents
CEO fraud prevention starts with understanding how CEO fraud works.
CEO fraud is a type of scam that uses social engineering attack techniques to exploit trusted relationships. It is also sometimes called “whaling” or business email compromise (BEC),
In a CEO fraud attack, a threat actor pretends to be a high-ranking company executive (often the CEO—hence the name—but it can also be the COO or CFO) to trick employees into downloading malware (for example ransomware), sharing confidential information, or making an unauthorized financial transfer.
What makes CEO fraud scams so successful and dangerous is that they’re highly targeted.
Fraudsters research potential victims online in an attempt to find as much information about them as possible. They then use this information to send individual employees personalized emails that seem to come from upper management.
Often, attackers will use an executive’s actual email address (after taking over their email account) or one that looks very similar (a practice known as “spoofing”).
Employee education and technical controls like email software can help with CEO fraud prevention. However, without a proactive effort to remove executive information from the internet, these kinds of solutions still fall short of full prevention.
Because most successful CEO fraud attacks rely on threat actors’ ability to find personal information about employees and executives, it is important to remove their data from online sources like data brokers.
The Role of Data Brokers In CEO Fraud
Before cybercriminals engage in CEO fraud, they conduct reconnaissance on potential targets. The goal here is to find the right people to phish, so things like org charts, job titles, and contact lists are very valuable.
Threat actors can use multiple methods to gather this information. For example, they can conduct open-source reconnaissance on social media platforms like LinkedIn and company websites.
However, looking for and gathering all this information from several different sources can be a time-intensive task.
As a result, cybercriminals are increasingly turning to data brokers for reconnaissance.
Data brokers and people search sites are websites that sell individuals’ personal and professional information to anyone who wants to buy it. Sometimes, this information (or a part of it) is also available for free.
Learn more: Data brokers: your comprehensive guide
Many business data brokers allow users to filter employees based on things like company name, location, job title, skills, years of experience, company revenue, keywords, and more.
For example, the below data broker lets users filter employees by the department they work in, management level, and when they changed jobs:
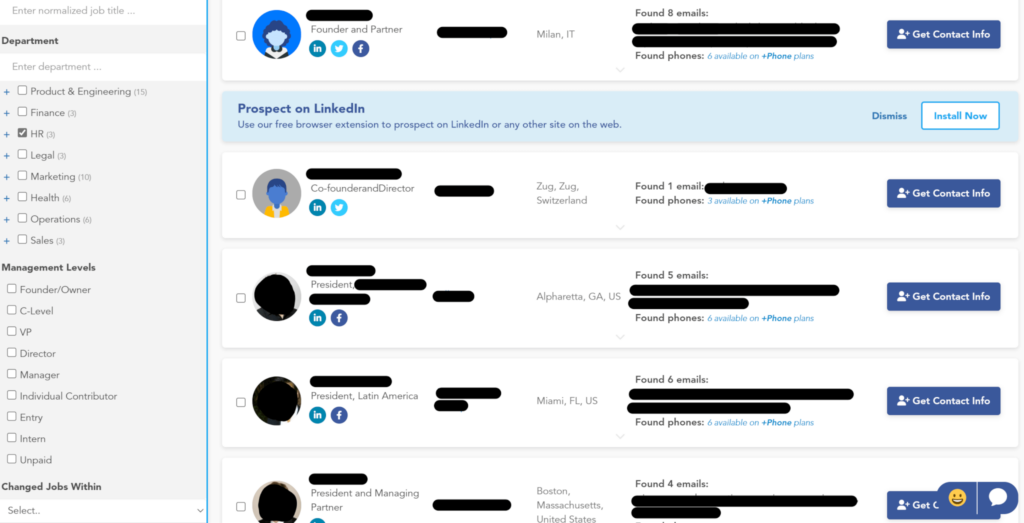
We know from recent leaks that cybercrime groups use data broker sources for target identification and to find people to “name drop” within emails.
How to Identify CEO Fraud
CEO fraud attempts are hard to identify because, unlike mass phishing emails, these attacks are frequently personalized to the recipient.
Learn more: The Ultimate Guide to Executive Privacy and Executive Security Online
However, if an email features one or more of the following, it may be a CEO fraud email:
- Sudden requests. This can be paying an invoice, making a wire transfer, buying gift cards, or disclosing sensitive information.
- Sense of urgency and authoritative tone. Scammers want targets to carry out their desired actions as quickly as possible.
- Changes to bank accounts or vendors. Cybercriminals will ask targets to make transfers to unusual bank accounts or vendors.
- Supposed “inaccessibility.” To prevent recipients from double-checking that their requests are genuine, cybercriminals will often say the sender is unavailable for a period of time (for example, they may say they’re at a business meeting, about to board a flight, etc.)
- Sender email addresses that are slightly off. Hackers that impersonate executives will often create email addresses that closely resemble those of actual executives (for example, bobbymarsh@agille.com versus bobbymarsh@agile.com).
CEO Fraud Prevention: 3 Tips
Here are three things organizations can do to minimize the risk of CEO fraud.
Educate employees about CEO fraud
Security awareness training is an important part of any company’s security policy and a great way to educate employees about CEO fraud and how to spot fraudulent emails that impersonate executives.
When they receive an email, employees need to:
- Double-check the email address and display name.
- Be on the alert for misspellings (especially of a company or executive names) and awkward wording.
- Not click on links/attachments within emails they suspect might be phishing attacks.
- Be suspicious of time-sensitive requests.
- Verify unusual/unexpected requests with the sender, preferably via the phone or in person.
Regular phishing and spear phishing simulations can give employees a better idea of the red flags to look out for.
Put in place technical controls
Technical controls are another important step in CEO fraud prevention.
CEO fraud cyber attacks often bypass email filters (including Google’s and Microsoft’s native filters), so it is crucial to have advanced email security software that can spot CEO fraud attempts (for example, urgent requests and spoofed domain names) in real-time and flag emails that are suspicious.
Password management and multi-factor authentication should also be implemented across the entire organization to protect important accounts and apps.
Opt employees out of data brokers
Neither employee training nor technical controls are 100% foolproof.
Highly targeted CEO fraud emails can bypass email tools and trick employees. To minimize the risk of that happening, it is critical to take away threat actors’ access to executive and employee personal information online.
Data brokers and people search sites are one of the largest sources of employee exposure.
Opting out executives and employees from data broker databases makes it harder for threat actors to find a) targets and b) details to personalize their emails.
The less personal data cybercriminals have about employees, the less realistic their emails will be, and the more likely it is that email software and/or employees will catch them.
CEO Fraud: Who Is At Risk?
Although every employee can benefit from data broker opt-outs, providing coverage to the entire organization may not be realistic for many companies, especially those with thousands of employees. In this case, identifying high-risk users can help narrow down who to protect.
CEO fraud often targets the following groups of people:
- Executives. Every executive is at risk of being impersonated in a CEO fraud attack.
- Finance and accounting. Employees within the finance and accounting departments are targeted for their ability to conduct money transfers.
- HR. Human resource employees have access to a lot of sensitive data, which makes them attractive targets to threat actors and a common patient zero in data breaches.
- IT. Cybersecurity and IT department employees are targeted for their access to password managers, emails, etc. If an attacker can compromise an IT staff member, they can likely gain entry into the entire organization.
CEO Fraud vs. DeleteMe
Technical controls and employee training are important in CEO fraud prevention, but personal data removal shouldn’t be overlooked either.
With attackers increasingly turning to data broker sources for reconnaissance, opting out of data brokers could mean the difference between a successful and failed CEO fraud attack.
How does DeleteMe privacy protection work?
- Employees, Executives, and Board Members complete a quick signup
- DeleteMe scans for exposed personal information
- Opt-out and removal requests begin
- Initial privacy report shared and ongoing reporting initiated
- DeleteMe provides continuous privacy protection and service all year
Your employees’ personal data is on the web for the taking.
DeleteMe is built for organizations that want to decrease their risk from vulnerabilities ranging from executive threats to cybersecurity risks.
