End User Security Awareness Training
Table of Contents
In this guide, we’ll explain what end user security awareness training is and what it looks like for a typical organization.
We’ll also discuss why training alone isn’t effective and what companies can do to reduce the likelihood that their end users will be targeted in attacks.
What Is End User Security Awareness Training?
End-user security awareness training is a training program that educates “end users” (typically company employees or organization members) about security.
The goal is to inform users about cyber threats and teach them how to protect themselves and their organization.
Why Is End User Security Awareness Training Important?
By educating their workforce about their role in cybersecurity, organizations can significantly mitigate the risk posed by human error, which is one of the biggest sources of data breaches.
While some security incidents happen due to negligence, like employees sending sensitive emails to the wrong recipient, criminals also use psychological manipulation to get end users to make security mistakes or share confidential information.
These manipulations often come in the form of phishing and business email compromise (BEC) attacks. In 2023, 73% of companies were targeted by BEC attacks, and 74% were targeted by spear phishing emails.
When employees receive these often convincing communications, it can be difficult to determine if they’re real or fraudulent.
That’s where security awareness training comes into play – it can teach employees how to recognize fraudulent messages and potentially malware- or ransomware-laden attachments, along with techniques for improving their overall security, like using strong passwords and backing up data.
What Does End User Security Awareness Training Look Like?
End user security awareness training is often conducted through a mixture of online courses, quizzes, workshops, regular updates, and practical exercises.
The specific type of training and the formats involved differ depending on the needs and vulnerabilities of the organization.
For example, some companies provide security advice daily through platforms regularly used by employees (such as Slack or Teams). According to CybSafe, 79% of office workers responded favorably to this delivery method, while a full 90% prefer to receive reminders through instant messaging apps. Using this method of frequent reminders (either daily or weekly) can double employees’ retention of their security training compared to those who receive it less frequently.
Your organization may make the training role appropriate by highlighting the risks affecting specific teams or departments. This is especially important if your organization handles sensitive data, as some team members will need more targeted training to learn the policies behind information security.
To determine what kind of training is appropriate for each department, ask yourself what technologies are used by employees within the department on a day-to-day basis and what threats or scams they’re likely to face.
If you make training relevant to what they’re doing, employees will be more likely to retain the information.
Key Aspects of End User Security Awareness Training
While specific components of a cybersecurity awareness training program will vary, common training modules will likely overlap for all involved.
With many people reusing previously compromised passwords, password security is a critical module to include. At the very least, it should teach employees how to create strong passwords that don’t contain easy-to-remember words, encourage everyone to change compromised credentials and enable multi-factor authentication.
Social engineering/phishing training is another important component, as phishing attacks are among the most common causes of data breaches. This module can cover everything from mass phishing campaigns to spear phishing and BEC attacks.
Other common training topics include physical security, sensitive information handling, mobile device security, remote work security, and incident reporting.
Why End User Security Awareness Training Is Not Foolproof
Regardless of how well you design your end user security awareness training program (or how often you provide it), remember that employee training is not foolproof.
Part of it comes down to convenience. Last year, 71% of trained employees admitted to taking risky actions, and 96% of them were fully aware that their actions were risky.
Even knowing that what they’re doing is potentially dangerous isn’t always enough to stop employees from carrying out that action anyway. It’s one thing knowing you need to stop using weak credentials. It’s quite another to start creating strong passwords you probably won’t remember.
Psychologist Bec McKeown acknowledges this, writing:
“What people don’t realize is that psychologically there is no direct link between awareness and behavior change. Most people believe that if you make people aware, they will do something about it. That is not true.”
You also can’t train against everything. Given how tailored social engineering attacks can be, it can be impossible for employees to make a connection between a phishing simulation and a real-world spear-phishing attack.
Organizations looking to minimize the possibility of data breaches and cybercrime should consider going beyond training programs.
How to Reduce the Risk of Personal Information Attacks
Cybercriminals use employee personal information to personalize their phishing emails, guess their account credentials, and impersonate them in BEC attacks.
Security awareness training can educate employees about these personal information threats, but it can’t guarantee that employees will be able to spot them in real time.
Rather than expecting employees to be able to catch these kinds of threats, it’s better to reduce the amount of ammunition (employee data) criminals can get their hands on. The best way to do that is through online footprint reduction.
Shrinking your online footprint generally involves several steps, including changing privacy settings on social media, limiting the amount of information posted on any public channel, and opting out of data brokers.
Data brokers, in particular, are a growing concern. They are companies that collect information about people and then sell it in the form of comprehensive profiles to anyone who wants them. Cybercriminals use data brokers to find targets and contacts to “name drop” in social engineering attacks.
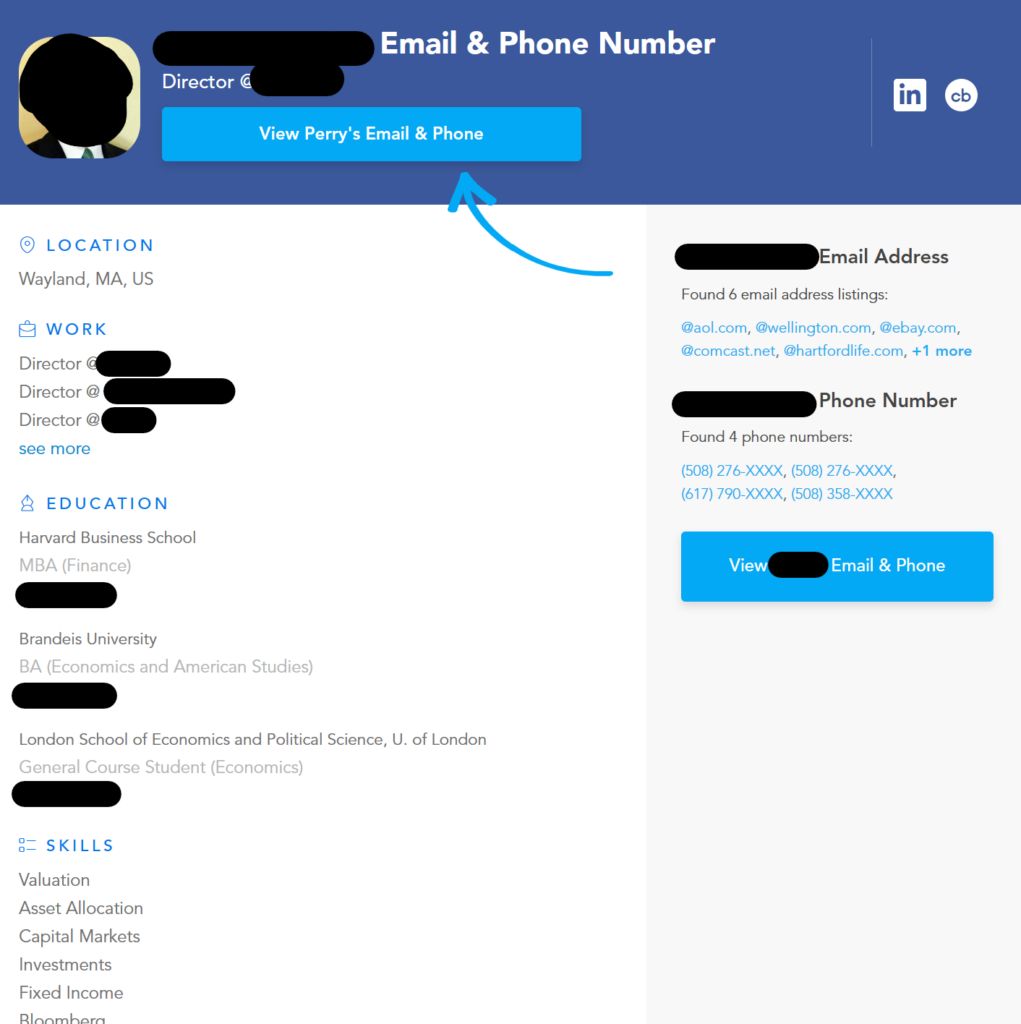
While it is possible to manually opt out of data brokers, employees would need to opt out of multiple brokers and do so repeatedly (brokers reactivate profiles when they find more information).
Alternatively, organizations can sign their employees to a data broker removal service such as DeleteMe, leaving the opting-out process in the hands of data professionals.
- Employees, Executives, and Board Members complete a quick signup
- DeleteMe scans for exposed personal information
- Opt-out and removal requests begin
- Initial privacy report shared and ongoing reporting initiated
- DeleteMe provides continuous privacy protection and service all year
DeleteMe is built for organizations that want to decrease their risk from vulnerabilities ranging from executive threats to cybersecurity risks.












