How Often Should Security Awareness Training Be Conducted
Table of Contents
The simple answer to “How often should security awareness training be conducted?” is: At least twice a year.
For a more granular answer (including why yearly training is insufficient and whether there’s such a thing as “too much” training), read the guide below.
We also explain why security awareness training alone is not enough and what other steps organizations can take to prevent employees from falling for spear phishing and other attacks.
How Often Should Security Awareness Training Be Conducted?
As a basic guideline, security awareness training should be conducted at least every 4 to 6 months, according to ISACA, an association focused on IT governance.
Studies have found that employees continue to retain the ability to recognize phishing attempts four months after training, but after six months, they begin to forget what they’ve learned.
After the 6 to 8-month window passes, employees’ skills are no longer much better than before the training.
Inside of the 4 to 6-month window, the exact frequency that will best suit your organization will depend on factors like:
- Size of your organization
- Complexity of your organization
- Compliance requirements
- Level of risk you face.
In any case, yearly training is not enough. Security awareness training should take place at least twice a year.
Can You Have Too Much Security Training?
Some experts believe you can have too much security training.
For example, employees who are overtrained in spotting spear phishing may lose productivity, according to Zinaida Benenson of the IT Security Infrastructures Lab at the University of Erlangen-Nuremberg, as per a CSOOnline article.
She says, “People’s work effectiveness may decrease, as they will have to be suspicious of practically every message they receive.”
Not everyone agrees, though.
Kevin Mitnick, once the world’s foremost hacker and now the head of Mitnick Security Consulting, strongly disagrees with that viewpoint.
“That would be like saying wearing a seat belt takes away the enjoyment of driving. Or locking your car makes people drive poorly. You wouldn’t blame the manufacturer if someone left his keys in the car and a thief drove off with the vehicle. The driver would be responsible,” he says.
The level of suspicion that you want your employees to utilize during their daily work will depend on your organization and your data security needs.
Lanze Spitzner, director of SANS Securing the Human, pointed out the need for balance.
“Not enough [suspicion] and bad guys get through. Too much and definitely trust and the ability to work together breaks apart,” he said.
As a rule of thumb, stick to whatever feels appropriate for your organization when it comes to training frequency – but focus on teaching employees to be skeptical when more scrutiny and distrust is essential, like when someone sends them a link (even if it’s someone they know) or if the company is going through a time of change or a significant financial event, like a merger and acquisition.
Security Training Is Important, But Not Something You Can Rely On 100%
While training is important, it should be just one of many tools in your utility belt to stop data breaches and other security incidents.
Even after receiving security awareness training, 44% of respondents in one survey admitted to reusing passwords across accounts and devices. Another survey found that only 45% of people change their passwords after data breaches occur.
People make mistakes, and they will keep making them out of habit.
Cybercriminals know this, too. 74% of all data breaches involve humans in some capacity, illustrating how easy it is for bad actors to get login credentials and how effective targeted spear phishing attacks can be.
Reducing the Risk of Personal Information Attacks
To improve their chances of success, criminals are increasingly researching their targets.
They use the information they find online to:
- Personalize their phishing campaigns.
- Impersonate executives and other employees in business email compromise attacks to trick victims into sharing sensitive information or clicking on malicious files.
- Guess passwords and security questions to corporate accounts.
In addition to offering regular security awareness training programs, it’s essential to give employees guidance on how to reduce their online footprint. Doing so will shrink the amount of information about them online, making it more difficult for criminals to execute the kind of personalized attacks mentioned above.
Consider educating employees on the importance of changing social media settings from public to private, limiting the amount of information they share on websites and forums, and opting out of data brokers.
Data brokers, in particular, represent a major vulnerability when it comes to employee data security. They are companies that collect public information about people and then sell this information to anyone willing to pay a small fee.
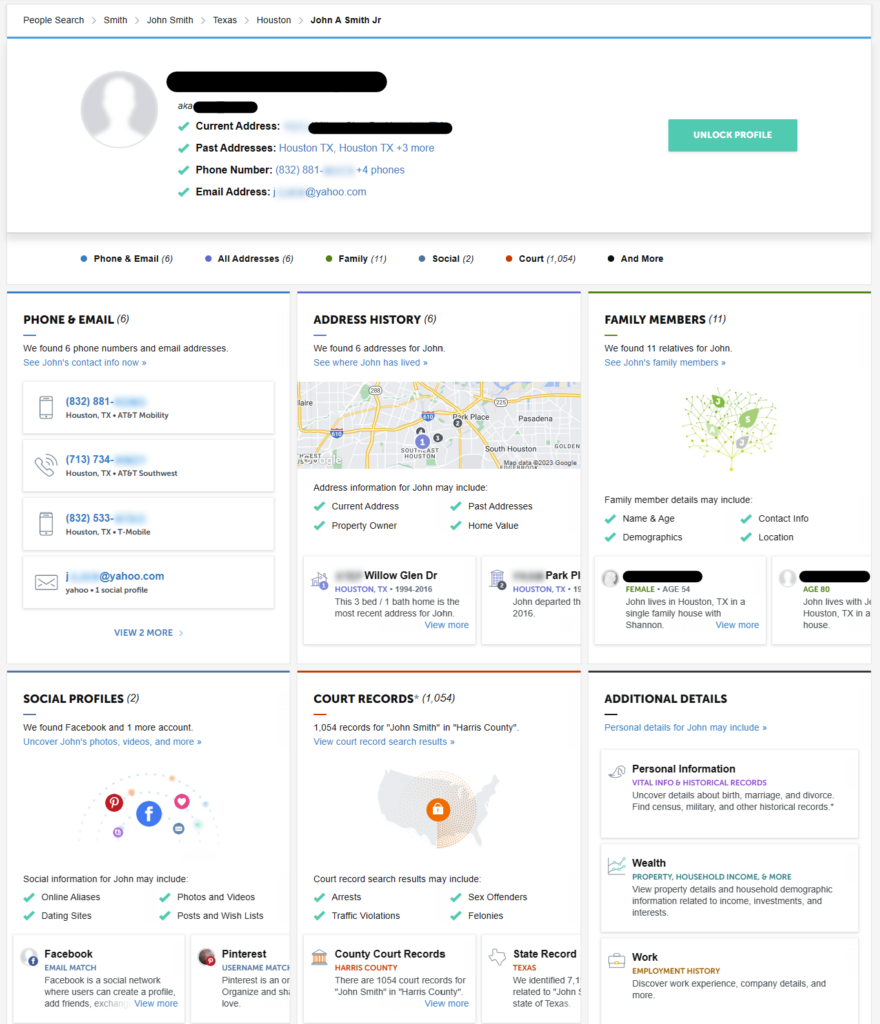
By obtaining data broker profiles (whether through buying them or hacking data broker databases), criminals can (and do) find a significant amount of information about employees in your organization. This can include data on their family (criminals now send phishing messages to employees’ family members) and who they report to within their organization (crucial for BEC attacks).
It is possible to opt out of data brokers, but employees will need to opt out of every data broker manually. They’ll also need to be diligent and repeat the process with the same data brokers whenever their profiles are reactivated (which occurs when new data is found online).
A better solution is for organizations to subscribe their employees to a data broker removal service such as DeleteMe, which can handle the data broker opt-out process on employees’ behalf.
- Employees, Executives, and Board Members complete a quick signup
- DeleteMe scans for exposed personal information
- Opt-out and removal requests begin
- Initial privacy report shared and ongoing reporting initiated
- DeleteMe provides continuous privacy protection and service all year
DeleteMe is built for organizations that want to decrease their risk from vulnerabilities ranging from executive threats to cybersecurity risks.












