OSINT: How Cybercriminals Use Open Source Intelligence for Social Engineering
Reconnaissance is how most cyber attacks start. Open-source intelligence (OSINT) is a powerful, free, and common way for cybercriminals to conduct reconnaissance.
In an interview with the YouTube channel Russian OSINT, a ransomware group LockBit 2.0 member alluded to using OSINT tools and techniques throughout their attacks. We also know that the now-defunct Conti group invested heavily in OSINT for intelligence gathering.
Although OSINT is a fundamental tool in all forms of cyber attacks, it is particularly important in social engineering. Speaking to DarkReading, TrendMicro’s vice president of threat intelligence, Jon Clay, said:
“The actors investigate their victims using open source intelligence to obtain lots of information about their victim [and] craft very realistic phishing emails to get them to click a URL, open an attachment, or simply do what the email tells them to do, like in the case of business e-mail compromise (BEC) attacks.”
Many security teams already use OSINT tools to do penetration testing against their own systems to identify potential gaps and vulnerabilities a real-world hacker might be able to exploit. This helps them reduce their attack surface.
However, few cybersecurity professionals audit employees’ personal data available on the open web to measure or mitigate social engineering risk. According to Verizon’s 2022 Data Breach Investigations Report, 82% of breaches recorded in 2021 involved some form of social engineering, with phishing via email accounting for more than 60% of breaches.
Numerous guides exist on using OSINT tools to gather intelligence and create convincing social engineering campaigns. Most specifically mention free data brokers and people search sites.
By reducing the amount of publicly available information about employees on people search sites, security teams can cut off important OSINT pathways and reduce their organization’s visibility to cybercriminals.
What is OSINT?
Open-source intelligence, or OSINT for short, is the act of passively gathering intelligence from publicly available sources and tools.
These might include:
- Social media platforms and professional networks, i.e., LinkedIn, Facebook, Instagram, etc.
- Newspapers, magazine articles, and media reports.
- Conferences, webinars, and public speeches.
- Public trading data.
- Data brokers like Spokeo and PeekYou.
- Web search engines like Google, Bing, etc. Techniques like Google Dorking can be used to narrow down results and also find information that would be difficult to find through standard search queries.
- Search engines for misconfigured or unprotected internet-connected devices like Shodan.
- Internet record listings like WHOIS Lookup to see who is behind a specific domain name.
- Data mining tools like Maltego.
- Network scanning tools like NMAP.
- Tools that automate the process of gathering intelligence, like the Python-based Spiderfoot (available on Windows, Linux, and Mac OS).
- Other tools like ExifTool for extracting metadata from images.
A popular OSINT methodology for finding free OSINT techniques (public records, data brokers, search engines, forums, blogs, social networks, WHOIS, the dark web, etc.) and OSINT data is the OSINT framework.
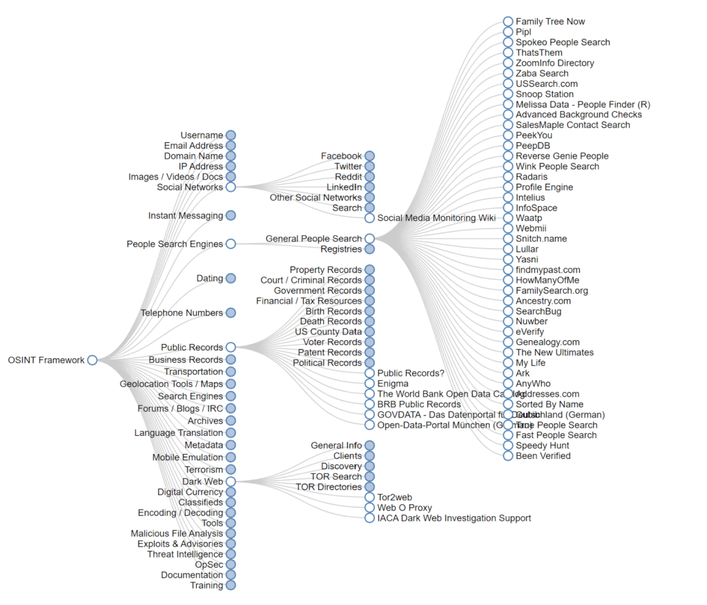
The OSINT framework is continuously updated, and anyone can suggest new resources via the OSINT framework GitHub page.
OSINT has many use cases aside from cybercrime. It is a practice also used by security researchers, law enforcement agencies, and journalists.
Trial and Error
As noted in a KnowBe4 webinar, “A Look Behind The Curtain: Open Source Intelligence (OSINT) Hacking Data Sources That Bad Guys Use,” finding exploitable, real-time sensitive data during an OSINT investigation is a trial and error process.
While some public sources offer up-to-date intel, others might host outdated or wrong data. As a result, attackers will try to connect data points to see what’s likely and what is misinformation.
For example, if you wanted to verify the information on a people search site, you might see if an address they list for an individual is correct by comparing it to an address on a property record database.
How Data Brokers Make OSINT Easier
Any social engineering attack, whether phishing or pretexting, starts with the attacker finding information about the target organization.
Questions like:
- What’s the org chart like?
- Who are the people working there?
- What are their job roles?
- What entities does the organization work with?
- What’s the company culture like?
Knowing the answers to these questions gives cybercriminals a good idea of who has access to what systems, what context would make sense to a target, and whom the email/text message should come from.
For example, according to the OSINT Curious Project, more conservative organizations with stronger hierarchies might be easier to phish using an authoritarian pretext because they tend to have a “do and don’t ask” culture.
Attackers frequently use LinkedIn and an organization’s website to discover this information.
Other useful resources include Corporate Governance Reports (for company structure), employee review websites like Glassdoor and Indeed (company culture), partner company/service providers’ case studies (to identify whom to impersonate), and people search sites (to find out a target’s interests and other relevant information that would make the social engineering campaign appear more believable).
Once threat actors know whom they want to go after, they will try to figure out their targets’ contact details, i.e., their email addresses and phone numbers. After all, if an attacker can’t reach their target, they can’t attack them.
There are many ways for cybercriminals to find out someone’s email address or phone number. Using people search sites/data brokers is one of them. Data brokers like Spokeo have both personal and professional phone numbers and emails. They pull the latter from business directories.
Unsurprisingly, ransomware groups like Conti have been proven to use data broker sites like SignalHire to gather information on targets, including contact information and contacts to “name drop” within phishing campaigns to make them look more legitimate.
Data brokers are a particularly valuable part of anyone’s OSINT toolkit because:
- According to our data, the level of personal information that data brokers have on individuals is continuously expanding as people spend more time on the internet. In the past, people search sites were populated primarily by “directory-style” data points, i.e., phone numbers, addresses, etc. Today, they include personal details like data on employees’ relationships, interests, and even IP addresses. Recent research shows that 40% of data brokers have executives’ home network IP addresses.
- Many people search sites allow anyone to see at least some of the information they have on an individual for free. Moreover, only a limited number of data brokers carry out background checks, so it’s easy for malicious actors to use their services.
- Even when people opt out of these databases, people search sites usually continue with their data collection and re-upload their profiles a few months later. As a result, data broker removal needs to be continuous. However, few people opt out of data brokers regularly because the process is time-consuming and frequently differs from one broker to the next. One OSINT guide explains how this can be used to the attacker’s advantage: “One of the methods to find people that opted out is to go the people search service, find a unique paragraph, do a quoted Google search on it, and find all of the domains that the company owns. There are chances that information your target removed from site A is now on site B.”
Managing Your Organization’s OSINT Footprint
What would you discover if you used open-source intelligence tools and techniques to look for human targets within your organization? An employee’s phone number? That your colleague is into gourmet coffee? The name of the CEO’s spouse and children?
Whatever information you find, threat actors can also see it. As attacks become more personalized, companies must work on shrinking their employees’ digital footprints and removing as much public data about them as possible.
- Employees, Executives, and Board Members complete a quick signup
- DeleteMe scans for exposed personal information
- Opt-out and removal requests begin
- Initial privacy report shared and ongoing reporting initiated
- DeleteMe provides continuous privacy protection and service all year
DeleteMe is built for organizations that want to decrease their risk from vulnerabilities ranging from executive threats to cybersecurity risks.












