Security Awareness Training Explained
Laura Martisiute
Reading time: 6 minutes

Table of Contents
Organizations around the world utilize security awareness training to make cyberattacks less likely.
In this guide, we’ll explain what security awareness training is, why it’s important, what it involves, and its limitations.
What Is Security Awareness Training?
Security awareness training is the process of educating employees, contractors, partners, and other stakeholders about why cybersecurity matters and how to avoid doing anything that might cause data breaches and other security incidents.
Like any training activity, the goal is for the participants to learn new knowledge and behaviors. You want employees to better understand their role in keeping their organizations’ assets safe and improve their ability to recognize potential threats online, such as phishing emails.
Cyber awareness training can also be legally necessary. Conducting security awareness training is a compliance requirement for organizations that need to follow industry and government regulations, like HIPAA or PCI.
Depending on the company, a cybersecurity awareness training program could be created and conducted internally, or a third-party provider may be brought in to help.
Why Is Security Awareness Training Important?
It’s hard to understate how frequently human error causes cyber attacks. Security awareness training does not take away human error, but it can do a lot to make employees less likely to enable attacks.
What Does Security Awareness Training Look Like?
Your company’s cybersecurity training program will be unique to your company’s operations.
However, there are some best security training practices you should follow. A core one is to train people often. Ideally, in small doses.
It’s generally agreed that annual in-person training and long-form computer-based security awareness sessions are ineffective in changing user behavior.
Instead, there should be frequent sessions throughout the year split into small modules that don’t overwhelm employees and combine different learning activities and formats, like on-demand courses, quizzes, and simulations, paired with actionable steps.
That way, it’s easier for employees to digest and retain the information and for cybersecurity and data privacy to remain top of mind at all times rather than just once a year.
Security Awareness Training Common Topics
Common topics for security awareness training programs include:
- Email security, for example, spear phishing simulations that teach employees how to spot suspicious emails requesting sensitive information or attachments that may contain ransomware or malware. Since phishing tactics are constantly evolving, phishing awareness training needs to continuously adapt to and highlight new cyber threats. To measure progress, it’s a good idea to do a baseline phishing test before you train people to see what the open rates for untrained individuals are like.
- Password hygiene, like educating end users about the dangers of password reuse and other bad habits such as writing passwords on sticky notes. Consider also setting mandatory password lengths, banning default passwords, and leveraging two-factor authentication.
- Physical security, such as training employees not to allow unauthorized persons into the building or office and reporting suspicious persons.
- Safe social media usage, including teaching employees not to overshare on social media.
- Remote work, like sharing information on how to make remote work environments secure.
- Desktop security, which focuses on locking terminals that aren’t in use and avoiding using unauthorized external devices.
- Wireless network security, including the do’s and don’ts when connecting to wireless networks, to minimize security threats.
Security Awareness Training Is Important, But Not Something You Can Rely On
Even frequent security awareness training sessions can’t completely eliminate human risk.
This is due to a few factors. First, there isn’t necessarily a link between awareness and behavior change. Studies show that employees still use easy-to-remember passwords even after they receive training. They also still fall for phishing scams.
Bec McKeown, founder and principal psychologist at Mind Science, says:
“What people don’t realize is that psychologically there is no direct link between awareness and behavior change. Most people believe that if you make people aware, they will do something about it. That is not true.”
Second, it’s impossible to cover all possible risk scenarios, especially those personalized to an individual or group of employees.
For example, with social engineering campaigns, it’s easy to spot “Nigerian prince” emails but much more difficult to tell if an email or text that references your personal details and seems to come from someone you know is real or fraudulent.
When it comes to passwords, employees may learn to use unique login credentials for corporate accounts but wind up including their personal information (like their spouse’s name or date of birth) in their passwords.
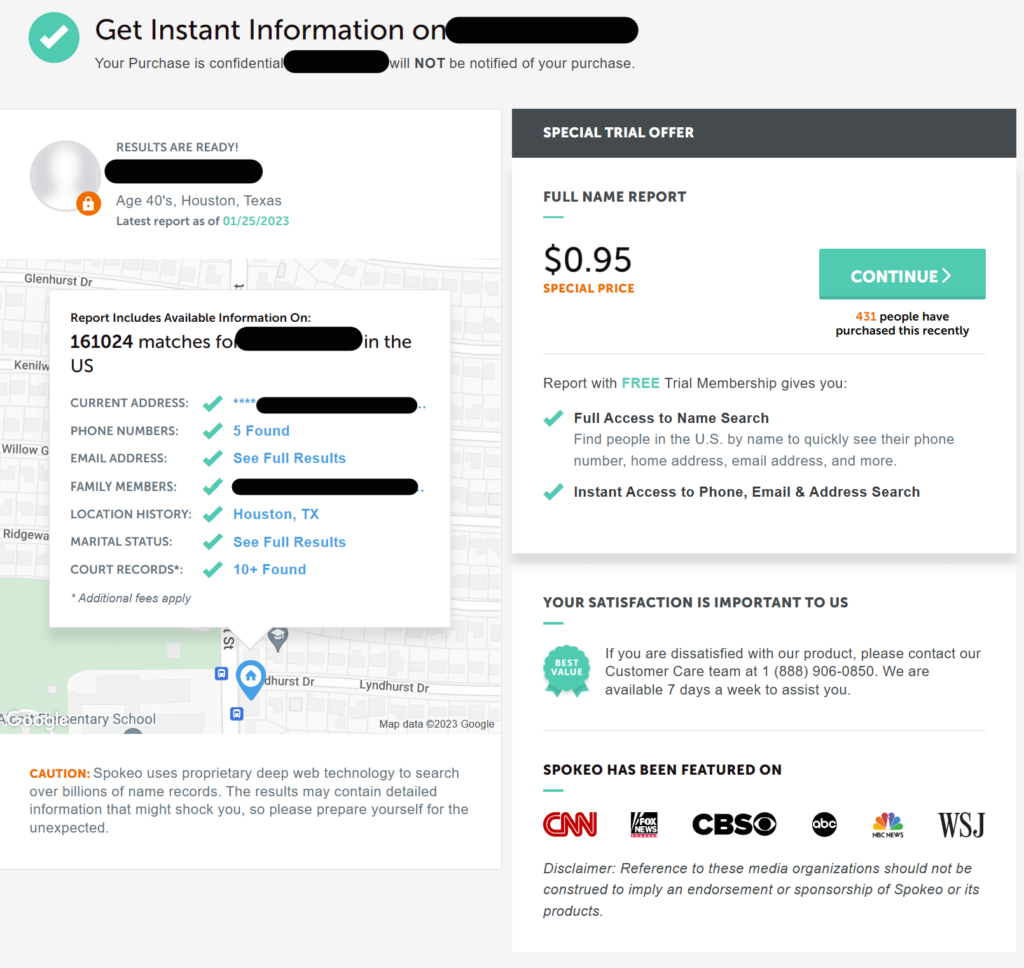
When that happens, the account is not actually secure. Cybercriminals can easily find employees’ personal information through various OSINT tools, including social media profiles, public records, and data brokers.
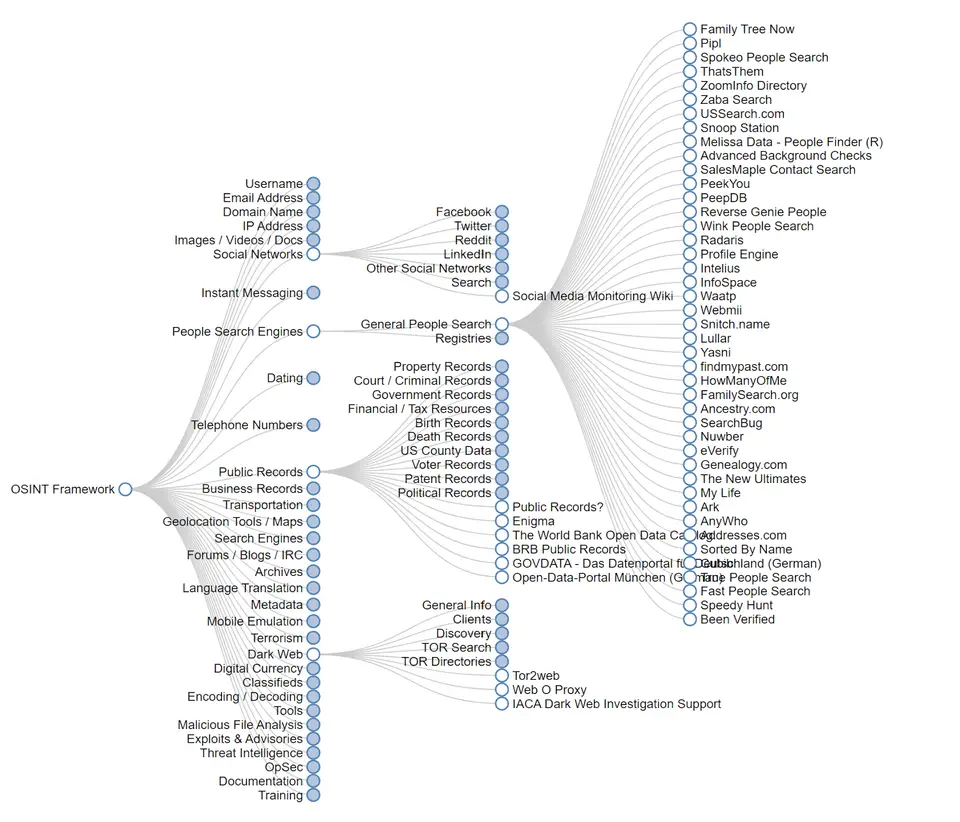
Data brokers, in particular, are worth a mention since they offer a lot of information in one place.
These companies gather people’s personal information from various sources, compile it into profiles, and sell these profiles to more or less anyone willing to pay for them.
Profiles can include employee names, email addresses (personal and professional), phone numbers, education and employment history, and family details.
How to Combat Personal Information-Based Attacks
There’s a secondary measure that can help ensure employees aren’t as vulnerable to cyber attacks: Digital footprint reduction.
Many cyber attacks utilize personal information, such as employee names, positions, emails, and so on.
Reducing the amount of information available about employees online can reduce the chances they’ll be targeted. If nothing else, it can limit the number of phishing attacks employees are exposed to.
To reduce employees’ online footprint, consider the following steps:
- Enrolling employees in a data broker removal service like DeleteMe. Internal chat transcripts from cybercriminal groups like Conti confirm that threat actors use data brokers for intelligence gathering.
- Educating employees about the risks of sharing personal details on social media and elsewhere online.
- Revisiting employees’ public biographies on company sites and social media accounts.
- Employees, Executives, and Board Members complete a quick signup
- DeleteMe scans for exposed personal information
Opt-out and removal requests begin - Initial privacy report shared and ongoing reporting initiated
- DeleteMe provides continuous privacy protection and service all year
DeleteMe is built for organizations that want to decrease their risk from vulnerabilities ranging from executive threats to cybersecurity risks.
Want more privacy
news?

Is employee personal data creating risk for your business?

















