Why Security Awareness Training Fails
Table of Contents
Among the many reasons why security awareness training fails, two in particular stand out to us:
- There’s no link between security awareness training and behavioral change.
- Personalized attacks are hard to spot and stop, even when individuals are trained to avoid phishing attacks.
In this guide, we’ll explain what security awareness training is and why it doesn’t always work as companies expect it to. We’ll also share some tips on how to minimize the risk of data breaches that exploit the human element.
What Is Security Awareness Training?
Security awareness training refers to information security programs within organizations that are designed to teach employees and other relevant stakeholders how to recognize cyber threats.
Training can consist of any number of modules, with common topics including email security (which may involve phishing simulations and malware-focused training), terminal security (including locking desktops that aren’t in use), and password strengthening.
The purpose of security awareness training programs is to prevent cyber attacks (social engineering, ransomware, etc.) from succeeding.
Why Security Awareness Training Fails
Teaching employees how to recognize phishing techniques and create strong passwords (among other things) should (theoretically) make the organizations they work for safer.
However, the reality is that most employees aren’t security experts, even trained ones.
Training scenarios take place in safe and controlled environments, and employees are generally passive participants. Meanwhile, actual cyber attacks are active and dynamic.
According to researchers, even after robust security training:
- 85% of employees continue to reuse passwords across business applications.
- 1 in 5 employees still fall for phishing scams.
Bec McKeown, founder and principal psychologist at Mind Science, says:
“What people don’t realize is that psychologically there is no direct link between awareness and behavior change. Most people believe that if you make people aware, they will do something about it. That is not true.”
Part of the problem is that employees typically only receive cybersecurity training once or twice a year, meaning that security isn’t at the forefront of their minds at any given moment.
Many employees also say the security awareness training they receive is outdated, too general, and too slow/not issued in real-time.
On the other hand, cybercriminals are constantly working to develop new techniques.
Besides utilizing new technical approaches, cybercriminals invest a significant amount of time working on ways to get employees to give them access to the company network.
This means cybercriminals are spending more time in the reconnaissance stage, researching employees through sources like data brokers. As a result, attacks are more likely to slip through email filters and employees’ own filters for what is expected to be a phishing attack.
Personal Information Attacks Require More Than Security Awareness Training
Let’s take a look at how cybercriminals use personal information in spear phishing and account takeover attacks.
Spear phishing
Most phishing attempts are relatively easy to spot due to unusual senders’ addresses or generic lures. These emails are sent out in the millions and have low chances of success.
That’s not the case for personalized phishing emails engineered to fool a particular employee or group of employees. In these cases, cybercriminals dive deep into their targets, acquiring personally identifiable information (PII) from anywhere they can find it. Emails of this nature can address employees by their first name and even reference superiors in the organization to build credibility.
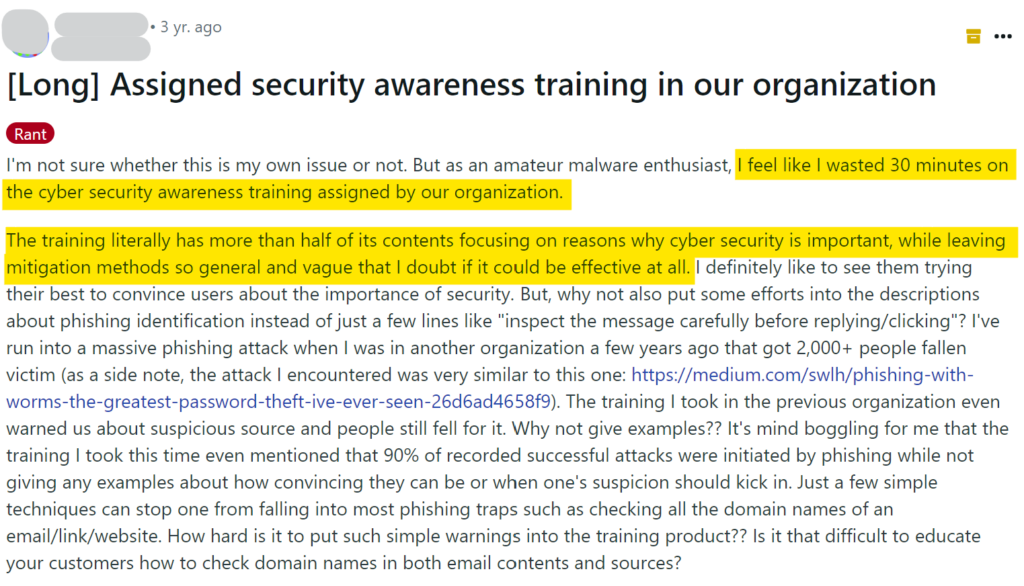
One of the top sources for PII is data brokers. Data brokers collect publicly available information about individuals and then sell this information as comprehensive profiles to anyone willing to pay a small fee.
One particularly notorious group of cybercriminals, Conti, is known for using data brokers to identify their spear phishing targets and determine whose name they should drop in the email to make it more convincing.
Some cybercriminals are also using data brokers to identify targets’ family members and use them as a way into corporate networks.
Personalized attacks can be very convincing, even to those who have received significant amounts of training – just ask senior Whitehouse cybersecurity advisors.
Account takeover
Once someone knows an employee’s background, it’s easy for them to start guessing passwords.
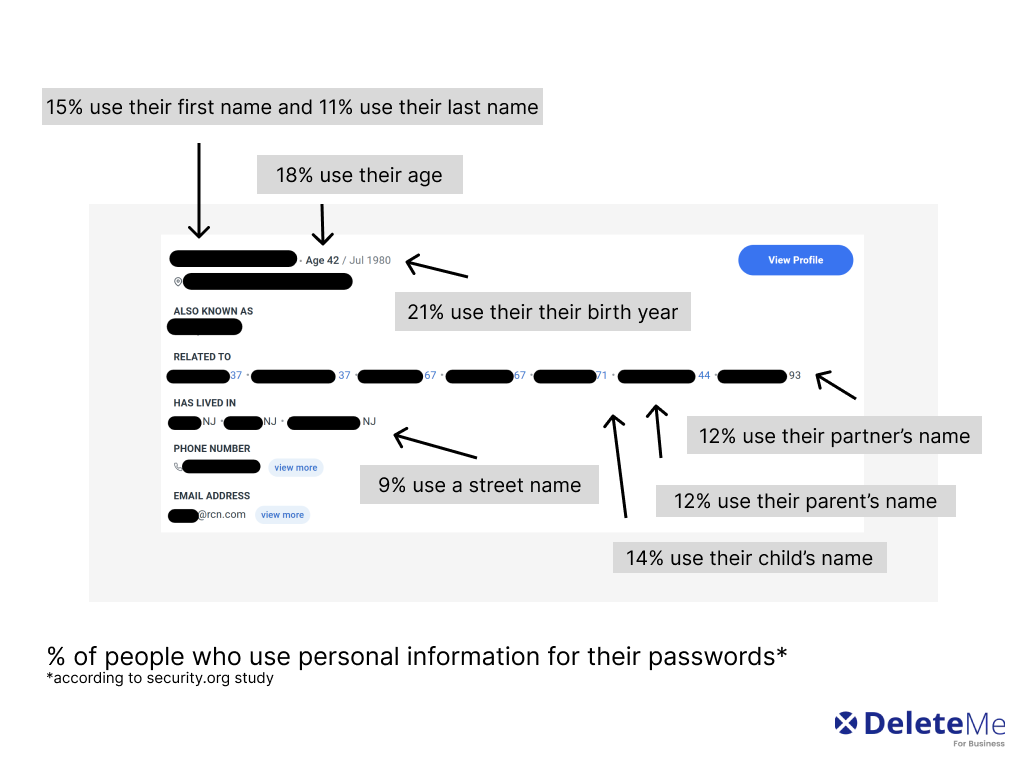
Most passwords are absurdly easy to guess, anyway. As NordPass’s annual password survey shows, the vast majority of people (including high-ranking executives) continue to use weak passwords like “123456,” “admin,” and “password.”
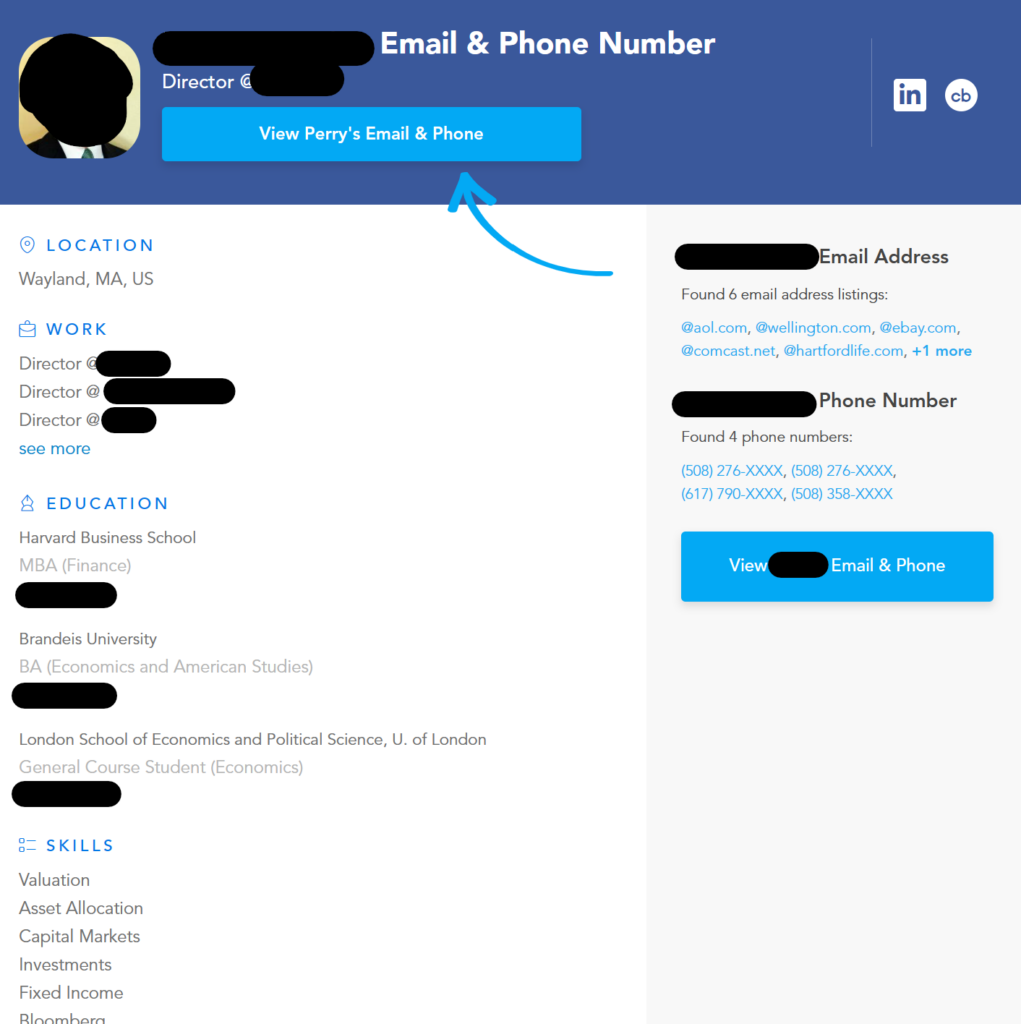
However, even when people try to create more complex login credentials, many end up leaning on their personally identifiable information (PII), whether it’s a birth date or a spouse’s name. But this kind of information is easy to find on a data broker profile.
All a cybercriminal has to do is acquire PII about an employee, load it into a password-cracking program, and then allow the program to try to guess their password over and over again until it gets it right.
How to Combat Personal Information-Based Attacks
Although security awareness training is important, organizations can’t rely on it alone to reduce their human attack surface, especially when it comes to personalized attacks against employees.
Besides fostering a security culture, organizations should also take steps to reduce their employees’ digital footprints. Potential measures include educating employees about the risks of over-sharing online and enrolling at-risk stakeholders in data broker removal services such as DeleteMe.
- Employees, Executives, and Board Members complete a quick signup
- DeleteMe scans for exposed personal information
- Opt-out and removal requests begin
- Initial privacy report shared and ongoing reporting initiated
- DeleteMe provides continuous privacy protection and service all year
DeleteMe is built for organizations that want to decrease their risk from vulnerabilities ranging from executive threats to cybersecurity risks.












