Stop ATO at the Source
Remove the Exposed Personal Data That Enables Credential Theft, MFA Bypass, and Impersonation
Account takeovers don’t start with a breach.
They start with open-source data. DeleteMe removes the personal information attackers use to seize control of accounts.
-
Automatically remove PII from data broker websites
-
Continuously monitor for new PII exposure
-
SOC II Type 2 certified

Stop ATO at the Source
Remove the Exposed Personal Data That Enables Credential Theft, MFA Bypass, and Impersonation
Account takeovers don’t start with a breach.
They start with open-source data. DeleteMe removes the personal information attackers use to seize control of accounts.
-
Automatically remove PII from data broker websites
-
Continuously monitor for new PII exposure
-
SOC II Type 2 certified

Trusted by more than 2,000 leading security teams





ATO Has Evolved, And It’s Personal
Modern account takeovers bypass your tech stack by targeting your people. Attackers no longer rely solely on stolen credentials, they’re levering freely available personal data on the open web.
Threat actors use publicly available personal data to:
- Answer security questions
- Bypass identity verification
- Manipulate helpdesk personnel
- Reset MFA methods or phone numbers
- Hijack email, payroll, and admin accounts
What fuels these attacks?
- Personal emails and phone numbers
- Home addresses and birthdates
- Family and pet names
- Past employers, schools, and affiliations
- Device fingerprinting data from public leaks
Where do attackers get it?
- Data brokers
- Breach dumps
- Social media
- People-search websites
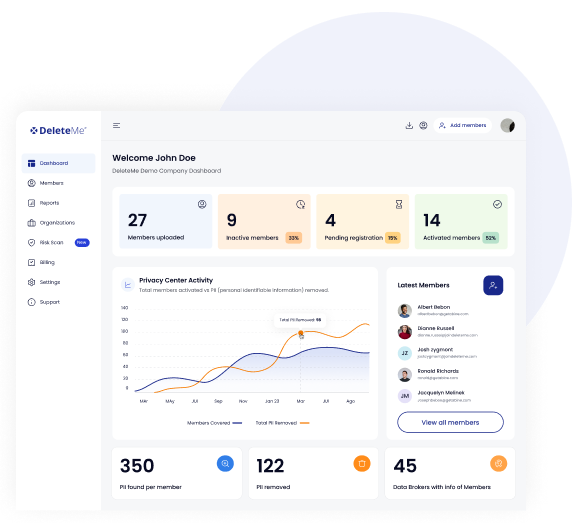
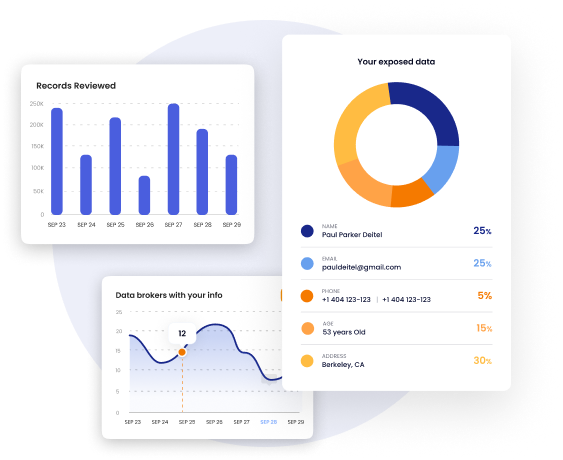
Proactive Personal Data Removal for ATO Prevention
DeleteMe continuously monitors and removes the personal data tied to your most at-risk employees, reducing the attacker’s ability to socially engineer their way into internal or third-party accounts.
You’ll Gain:
Automated Open Web Data Removal – We remove exposed personal data from hundreds of data brokers, aggregators, and search sites — continuously.
Real-Time Monitoring & Alerts – Get alerts when sensitive PII resurfaces: by user, department, or risk category.
ATO Risk Visibility – Track exposure by high-privilege roles: IT admins, finance teams, HR, and executive assistants.
MFA Resilience & Helpdesk Protection – Prevent MFA bypasses and fraudulent resets by removing personal data used in identity validation workflows.
Reports for IAM & Audit Compliance – Provide documented risk reduction progress to auditors, regulators, or your board.
Built for Security Teams Protecting People
Whether you’re running executive protection, security awareness, or threat prevention programs, DeleteMe scales to match your org.
Who We Work With:
- Fortune 500 CISOs
- Threat Intelligence Teams
- Security Awareness & Training Managers
- Security Leaders at Financial, Tech, Government, and Healthcare Orgs
What They Say:
“DeleteMe is a critical layer in our security stack, removing exposed PII is essential to protecting our employees and reducing risk. It’s become a core part of how we defend our organization’s privacy posture in today’s threat landscape.”
— Melissa Lee, Principal Behavioral Engineer, yahoo!
Complements Your IAM & Security Stack
DeleteMe works alongside:
- SSO, MFA, and PAM solutions (Okta, Duo, CyberArk)
- Helpdesk and access recovery policies
- Email security platforms
- ATO monitoring and fraud detection tools
Identity protection isn’t complete without data exposure defense.
Roles Most Targeted for ATO:
- Executives – for access to strategic data and email accounts
- IT/Admins – to escalate privileges or disable security tools
- Finance Teams – to reroute payments or payroll
- HR Staff – for employee PII and benefits fraud
- Customer Support – for social engineering entry points
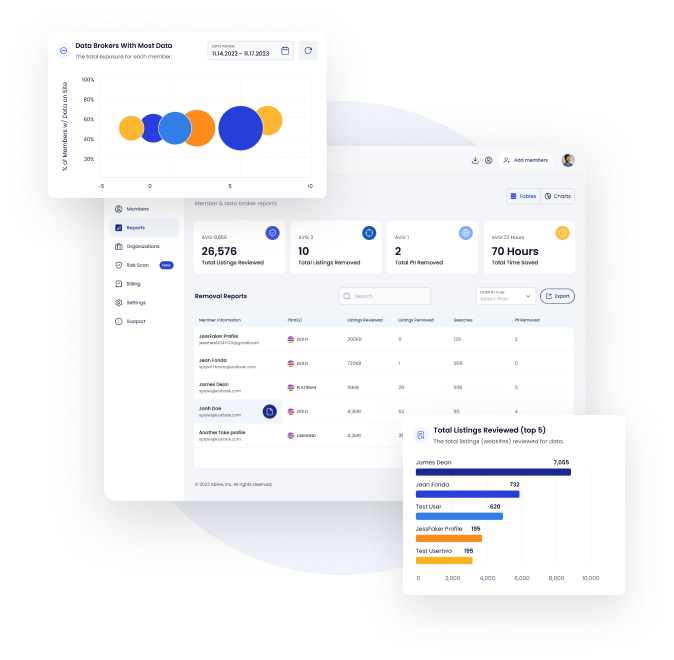
Interested in Seeing Your Organization’s Risk Exposure? Contact us.
Please fill out the information below and a DeleteMe representative will get back to you.
Please fill out the information below and a DeleteMe representative will get back to you.














