Creating an Executive Cyber Security Training Program That Works Against Personalized Threats
Laura Martisiute
Reading time: 8 minutes
Table of Contents
TL;DR: Executive cyber security training helps defend executives against some cyber risks. However, training must be augmented with data removal to protect executives from personalized threats.
- Personalized threats are threats that target executives specifically by using detailed information about them.
Personalized threats defeat executive cyber security training because they use personal data (such as professional roles, contact details, and even family member information) to create highly convincing and contextually relevant attacks.
- DeleteMe supplements executive cyber security training by keeping personal data away from cybercriminals.
AI advancements make it easier for criminals to build sophisticated attack chains.

Companies that protect their executives against AI attacks will increasingly depend on combining cybersecurity training with personal data protection solutions.
Combining training with personal data protection covers two bases, making it less likely an executive will engage with a personalized cyber threat and making it harder for someone to create that threat in the first place.
Executive Cyber Security Training Has Never Been More Crucial
Executives are attackers’ prime targets.
According to one recent study:
- 72% of US senior executives were targeted at least once by a cyberattack in the last 18 months.
- 69% of respondents whose company’s senior executives were previously targeted say cyberattacks against senior staff have increased.
Criminals target executives because:
- Executives often have direct access (as administrator) or control over people with access to their organization’s most valuable assets. Bank accounts, customer data, the ability to approve large transactions, etc.
- They tend to be “public personas,” i.e., their personal information is usually available on social media, company websites, and professional networks. Attackers can use this data in their attacks, for example, to create personalized phishing attacks that are hard to detect.
- People with packed schedules (like executives) are more likely to make quick decisions or overlook subtle red flags (e.g., in social engineering attacks). It might even make them skip cyber training. In the study mentioned above, among the companies who said they don’t prioritize extra cyber training for senior executives, 34% said this was due to resistance from senior leadership to participate in training due to time constraints.
How to Train Executives to Withstand Personalized Threats
How do organizations protect their executives against modern threats? We see secure organizations build training programs with three core training content and process inputs.
1. Put a spotlight on social engineering
Attackers often target people through the same hooks that sales might use, e.g., needs, desires, wants, and (most of all) points of contact they already know.
Social engineering attacks, such as phishing, spear phishing, and pretexting, all rely on hooking a target executive with a point of relevance, like a hobby they have, the school they went to, their job responsibilities, etc., that will get them to put their guard down and engage with what is really a scam.
A real-world example of a personalized spear phishing campaign targeting executives is the attack on the French cinema group Pathé.
Here, cybercriminals sent Pathé Nederland director an email that looked like it came from the chief executive of the French parent company, falsely claiming a need for urgent funds related to a business acquisition.
Despite a few inconsistencies, the email successfully manipulated internal communications, leading to multiple fraudulent transfers before the deception was uncovered.
The above campaign – and many executive social engineering attacks – is only made possible when an attacker can get an executive’s email address alongside their job description and company hierarchy.
2. Have a game plan for personalized threat campaigns
Executive social engineering campaigns, like the one in the previous point, rely on attackers being able to find executives’ personal information, like their email addresses, roles, and communication styles.
The result is highly personalized messages that increase the likelihood of the executive engaging with the phishing attempt.
All the security awareness training in the world won’t work against an attacker who really “knows” their target. Just like a great cold sales pitch, a personalized phishing attack will break down someone’s guard just enough to get them to engage and move deeper into the scam.
What’s worse is that security awareness training often focuses on generic tactics and common phishing scenarios. Generic training is seen by executives as something they must do to “tick a box” alongside 100 other priorities.
Personalized social engineering attacks (designed with detailed knowledge of the target’s personal and professional life) are not picked up.
3. Work backward from the methods criminals use to target executives
Criminals can use a variety of methods to gather executives’ personal information for personalized attacks.
Common techniques include:
- Open Source Intelligence (OSINT)
Publicly available information from company websites, press releases, annual reports, and professional profiles (e.g., LinkedIn) can reveal executive details and email formats. - Social media
Social platforms such as Twitter, Facebook, and LinkedIn often provide clues about an executive’s contact information and professional networks. - Domain and email reconnaissance
Tools that analyze domain registrations or company email structures (e.g., common email patterns like firstname.lastname@company.com) allow criminals to figure out potential email addresses. - Data breaches
When companies or third parties experience breaches, leaked databases may include executive contact details that criminals can use for targeted attacks. - Data brokers
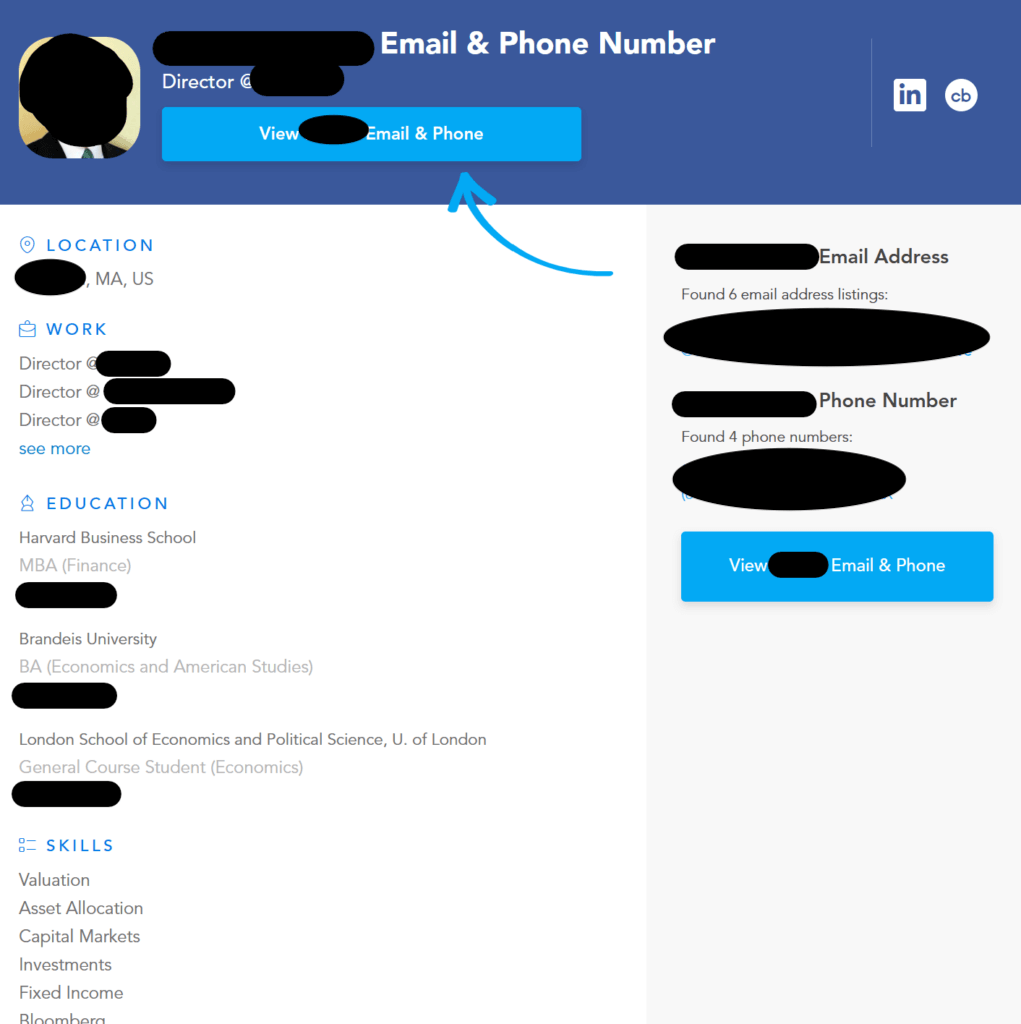
People search sites and B2B data brokers share executives’ personal information (including their email address, phone number, family member details, education history, etc.) in one place.
When it comes to data brokers, we know from leaked criminal chat transcripts that attackers buy executive data from data brokers.
It’s easy to see why. Data brokers are fantastic tools for determining spear-phishing targets and finding contacts to “name drop” in social engineering attacks.
Here’s an example of an executive’s profile on a B2B data broker website:
Many B2B data brokers also include org business charts.
Criminals leverage org charts to further personalize their attacks by:
- Identifying key decision-makers
By knowing who holds power within the organization, attackers can target individuals with the authority to make critical decisions or access sensitive data. - Tailoring the message
With details on roles and relationships, criminals can craft messages that appear to come from a trusted colleague, superior, or even a subordinate. - Simulating internal communication
Knowledge of departmental structures could allow attackers to mimic the language, tone, and content of legitimate internal communications, making their phishing emails or other social engineering attempts more convincing.
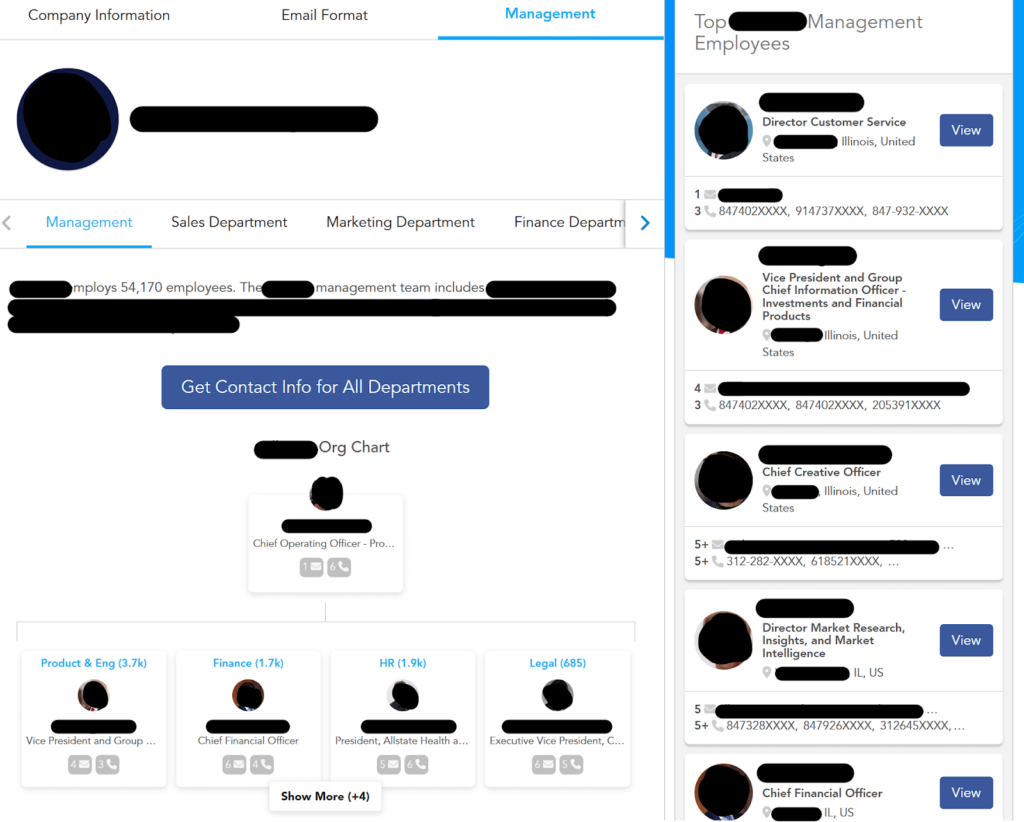
Attackers also love to use people search sites (“regular” data brokers).
These sites include personal details like potential family members, marital status, and social media links – data that criminals can further make use of in their campaigns.
AI Has Made It Easier to Launch Cyber Attacks Against Executives
AI tools are making it faster and easier for criminals to gather information about executives by automating high-risk spear phishing operations, including data collection.
A recent Harvard study found that AI successfully gathered precise and valuable information in 88% of cases. AI can also analyze large amounts of data on an executive’s tone and style, making it easier to create persuasive scams.
As per the Harvard study:
“AI enables attackers to target more individuals at lower cost and increase profitability by up to 50 times for larger audiences.”
Secure Companies Build Training Programs with These 2 Inputs
In the next five years, companies that combine personalized executive cybersecurity training with active data removal solutions will stop far more attacks against executives than their peers.
1. Up-to-date cyber security training content
Training programs should address the risks of personalized social engineering and spear phishing and include real-world examples and simulations demonstrating how attackers could leverage executives’ personal data.
Ensure training materials are frequently updated to reflect evolving tactics (particularly important with advancements in AI and data mining techniques).
2. Executive data footprint management
Educate executives on the importance of reducing how much personal and professional information they share online.
Advise executives on the benefits of regularly reviewing and cleaning up their online profiles. This includes removing unnecessary personal details that attackers could exploit.
Work with cybersecurity professionals like DeleteMe to identify and remove personal and professional information from data broker sites. This reduces the chance of attackers accessing personal details about executives.
Boost Your Executive Cyber Security Training Program with Personalized Data Removal
By combining specialized training with proactive steps to reduce digital exposure, organizations can better protect their executives from sophisticated, personalized cyber threats.
- Employees, Executives, and Board Members complete a quick signup
- DeleteMe scans for exposed personal information
Opt-out and removal requests begin - Initial privacy report shared and ongoing reporting initiated
- DeleteMe provides continuous privacy protection and service all year
DeleteMe is built for organizations that want to decrease their risk from vulnerabilities ranging from executive threats to cybersecurity risks.
news?

Is employee personal data creating risk for your business?


















