Stop Business Email Compromise Before It Reaches the Inbox
Remove the Personal Data That Fuels Social Engineering, Impersonation, and Financial Fraud
BEC isn’t just an email problem.
It’s a people problem and it starts with publicly exposed personal data.
DeleteMe removes that data before attackers can use it.
-
Automatically remove PII from data broker websites
-
Continuously monitor for new PII exposure
-
SOC II Type 2 certified

Stop Business Email Compromise Before It Reaches the Inbox
Remove the Personal Data That Fuels Social Engineering, Impersonation, and Financial Fraud
BEC isn’t just an email problem.
It’s a people problem and it starts with publicly exposed personal data.
DeleteMe removes that data before attackers can use it.
-
Automatically remove PII from data broker websites
-
Continuously monitor for new PII exposure
-
SOC II Type 2 certified

Trusted by more than 2,000 leading security teams





Why BEC Still Works — Even with Secure Email
Business Email Compromise is one of the costliest cybercrimes — because it doesn’t rely on malware. It relies on human trust, timing, and believable impersonation.
Attackers use open-source data to create highly convincing scams that result in:
- Fraudulent wire transfers
- Vendor impersonation
- Payroll diversion
- Gift card scams
- CEO/CFO impersonation
- Executive assistant manipulation
What Enables These Attacks?
- Names, job titles, and reporting structures
- Direct phone numbers and personal emails
- Executive travel schedules and meeting references
- Relationship data (e.g. assistants, vendors, family members)
- Writing styles and signatures pulled from public sources
This data is harvested from:
- People-search and broker sites
- Leaked directories and LinkedIn profiles
- Conference bios and press releases
- Social media accounts
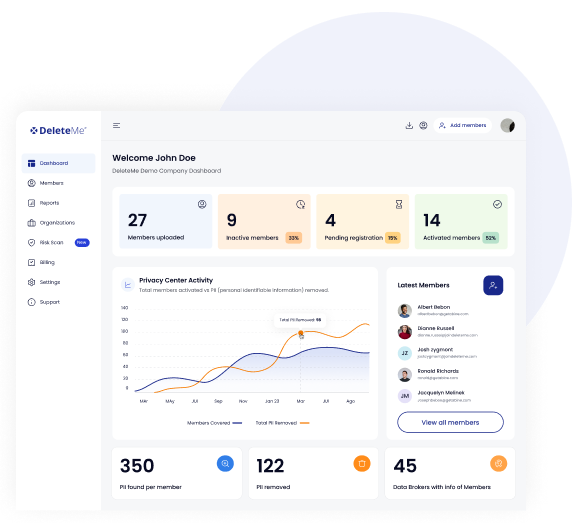
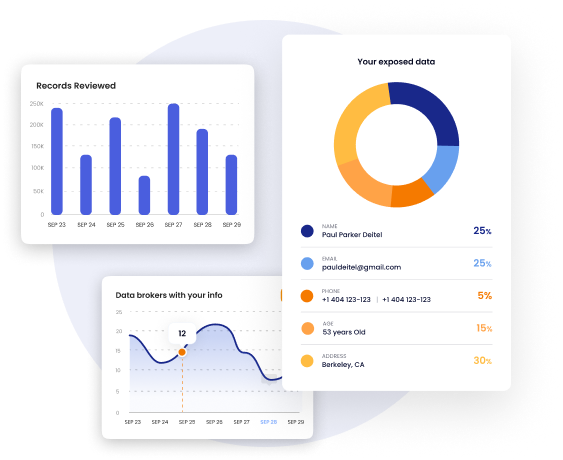
Exposure Elimination for BEC Defense
DeleteMe proactively removes your employees’ personal data from the open web — the very data attackers use to plan and execute BEC attacks.
Your BEC Defense Gets Stronger With:
Continuous Data Broker Removal – We remove PII from hundreds of high-risk sources, targeting attacker reconnaissance tools.
Role-Based Monitoring – Focus protection on executives, finance teams, executive assistants, legal, and HR, the most spoofed roles.
Exposure Dashboards & Alerts – Get visibility into organizational risk posture, including who’s being re-exposed and when.
Supports Fraud & Incident Response Teams – Generate exposure intelligence to support red teaming, IR playbooks, and pretext detection.
Audit-Ready Reporting – Track and report on digital risk mitigation efforts by role or department.
Built for Security Teams Protecting People
Whether you’re running executive protection, security awareness, or threat prevention programs, DeleteMe scales to match your org.
Who We Work With:
- Fortune 500 CISOs
- Threat Intelligence Teams
- Security Awareness & Training Managers
- Security Leaders at Financial, Tech, Government, and Healthcare Orgs
What They Say:
“DeleteMe is a critical layer in our security stack, removing exposed PII is essential to protecting our employees and reducing risk. It’s become a core part of how we defend our organization’s privacy posture in today’s threat landscape.”
— Melissa Lee, Principal Behavioral Engineer, yahoo!
Interested in Seeing Your Organization’s Risk Exposure? Contact us.
Please fill out the information below and a DeleteMe representative will get back to you.
Please fill out the information below and a DeleteMe representative will get back to you.














