Stop Social Engineering at the Source
Eliminate the Personal Data Fueling Human-Targeted Attacks
Social engineers don’t hack infrastructure — they hack people.
DeleteMe helps security teams shut down open web exposure that attackers use to impersonate, manipulate, and breach.
-
Remove your PII from data brokers and more
-
Continuously monitor for new exposures
-
SOC II Type 2 certified

Stop Social Engineering at the Source
Eliminate the Personal Data Fueling Human-Targeted Attacks
Social engineers don’t hack infrastructure — they hack people.
DeleteMe helps security teams shut down open web exposure that attackers use to impersonate, manipulate, and breach.
-
Remove your PII from data brokers and more
-
Continuously monitor for new exposures
-
SOC II Type 2 certified

Trusted by more than 2,000 leading security teams





Your people are your greatest asset — and your most vulnerable attack surface
Even your awareness training can’t help if attackers already know everything about your employees.
Attackers use open-source data to create highly convincing scams that result in:
- Fraudulent wire transfers
- Vendor impersonation
- Payroll diversion
- Gift card scams
- CEO/CFO impersonation
- Executive assistant manipulation
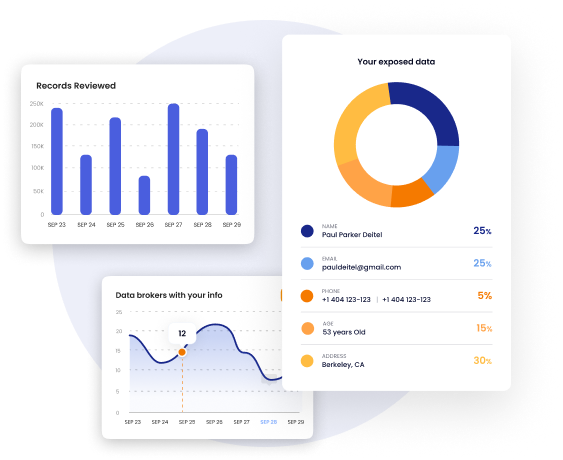
This data is harvested from:
- People-search and broker sites
- Leaked directories and LinkedIn profiles
- Conference bios and press releases
- Social media accounts
- Public filings and databases
What Enables These Attacks?
- Names, job titles, and reporting structures
- Direct phone numbers and personal emails
- Executive travel schedules and meeting references
- Relationship data (e.g. assistants, vendors, family members)
- Writing styles and signatures pulled from public sources
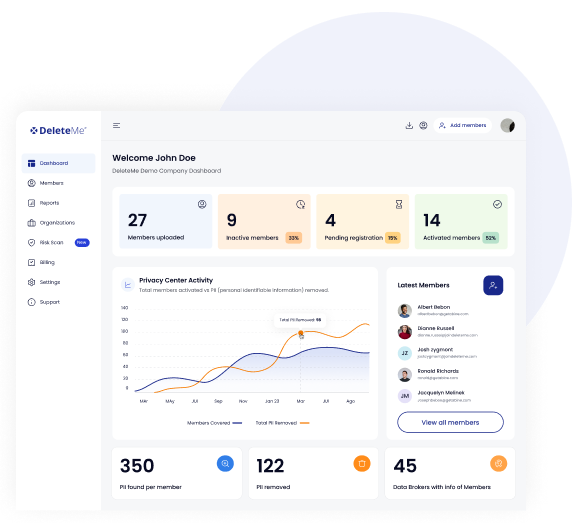
Proactive Exposure Reduction Without the Manual Cycles
DeleteMe removes your employees’ personal information from the open web, continuously and at scale.
With DeleteMe, your team gets:
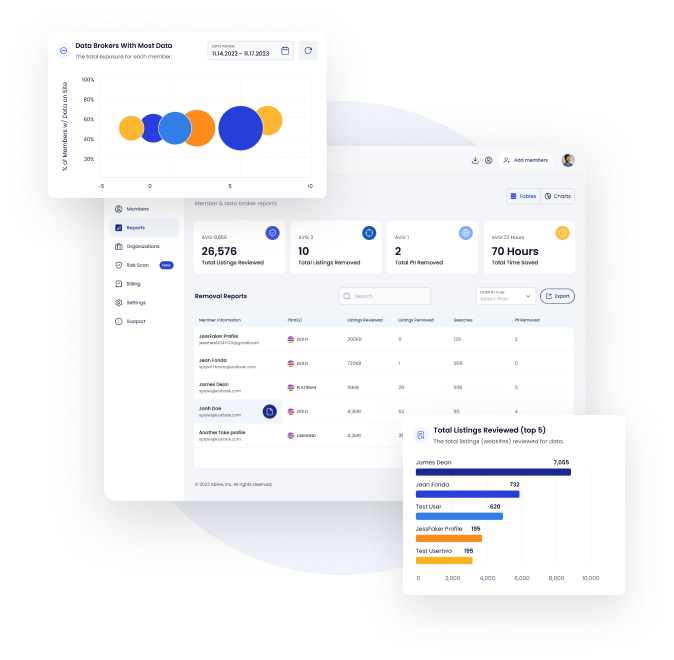
Comprehensive Monitoring – Track exposure across hundreds of data brokers, people-search sites, and leak aggregators.
Automated Opt-Out & Removal – We handle the takedown process end-to-end. No tickets, no scripts, no headcount needed.
Risk-Based Reporting – Get visibility into organizational exposure by role, department, or risk level — perfect for board reporting and red teaming.
Employee Privacy Shields – Reduce the effectiveness of impersonation and pretexting across your most targeted roles:
-
Executives
-
Security and IT Personnel
-
Finance teams
-
Any public facing or high risk roles
Built for Security Teams Protecting People
Whether you’re running executive protection, security awareness, or threat prevention programs, DeleteMe scales to match your org.
Who We Work With:
- Fortune 500 CISOs
- Threat Intelligence Teams
- Security Awareness & Training Managers
- Security Leaders at Financial, Tech, Government, and Healthcare Orgs
What They Say:
“DeleteMe is a critical layer in our security stack, removing exposed PII is essential to protecting our employees and reducing risk. It’s become a core part of how we defend our organization’s privacy posture in today’s threat landscape.”
— Melissa Lee, Principal Behavioral Engineer, yahoo!
-
SOC II Type 2 certified and ISO 27001 Compliant
-
Privacy management through a central Admin Portal
-
Integrations with SSO and Identity Management Systems
-
Org-wide and user-level reporting
Defense in Depth, Down to the Human Layer
Most social engineering attacks don’t fail because of a lack of technology — they succeed because attackers know too much.
DeleteMe removes that advantage.
Add personal data exposure management to your Zero Trust and Social Engineering Prevention playbooks.
Learn more about the risks to executives and employees from exposed PII.
Interested in Seeing Your Organization’s Risk Exposure? Contact us.
Please fill out the information below and a DeleteMe representative will get back to you.
Please fill out the information below and a DeleteMe representative will get back to you.














