Use These Doxxing Tools to Self-Dox
- Doxxing
- Is Doxxing Illegal?
- Use These Doxxing Tools to Self-Dox
Table of Contents
If you’re going to dox or “drop docs” on yourself, you’ll need a list of doxxing tools to make the job easier.
In this guide, we’ll look at some of the open source (i.e., freely accessible) tools you can use to find information about yourself before it gets into the wrong hands, including search engines, people search sites, email permutators, public records, maps, and more.
Search Engines
Search engines such as Google are an easy first stop if you’re looking for personal information.

Go to Google Search, Bing, DuckDuckGo, or your preferred search engine and type in your full name, account username, phone number, home address, or whichever identifying detail you’d like to look up on yourself.
Note: You should open a private tab or incognito browsing window if you’d like to see what an anonymous user would see (rather than the customized results you typically get).
You may need to combine some of your details, such as your name, city, or occupation. For best results, think of what someone may know about you and make that part of your search query.
If you’re using Google, you can use some simple boolean commands (just like a potential doxxer would do). Try typing in [First name]+[Last name], adding in your own name, and keeping the plus sign. Or [First name] [Last name]+[birthdate]. Or try replacing [birthdate] with your place of work, home city, home address, or the place you went to school.
You should also try searching for your online account usernames and email addresses, either alone or in combination with your other details.
On both Google and Bing, you can try additional search operators to see what comes up. Use a site-focusing command like site:facebook.com to search for results on a particular website. Or use the asterisk (*) to fill in a blank – such as [First name] * [workplace]. If someone knows your first name and that you work at a particular location, for example, they’ll be able to find out more using that.
It’s important to be as creative as your potential doxxer might be.
Every site that comes up as a match for any search queries related to you could lead to more personally identifiable information, giving doxxers a trail to follow that could lead to online harassment, cyberbullying, swatting, or even in-person attacks.
If it’s a site you can access and remove the information from, do so.
Tip: You can set up a Google alert to be notified whenever a new result with your details turns up on Google search. To do so, visit Google Alerts, log in if needed, and make an alert for the result you’d like to be notified about (name, email address, phone number, etc.).
Learn more in our guide on how to remove doxxing content on Google.
People Search Sites
Some of the first results you’ll get when you look up your name on a search engine are for people search sites (aka data brokers).
These sites (such as Whitepages, Spokeo, People Finder, and so on) sell profiles on people for a minimal fee, with each profile consisting of compiled public information about you.
If someone has your name, phone number, email, or even your username, they will be able to find your profile and request access to all the personal data the people search site has on you.
The amount of information in a data broker profile can be quite significant and may include personal details like your employment history, education, nearest relatives, and more.
The good news is that you can opt out of people search websites, typically using a form on the website that has a profile on you or by sending them an email making it clear who you are and that you’d like to opt out.
Because the opt-out process for each data broker is different, we’ve put together free, step-by-step guides on how you can remove yourself from major data brokers.
The bad news is that data brokers frequently refresh their profile databases. This means that even if you opt out from a data broker once, they may re-add your profile when they collect more data about you.
To escape this repetitive cycle, subscribe to a data broker removal service like DeleteMe that continuously handles removal requests on your behalf.
Username Search Engines
If you use the same username on multiple websites, anyone who knows your username on one platform can also find you on other platforms. This is even easier using username search engines, which show where the same username is in use.
Here are a few username search engines to try:
Email Permutators
If someone knows your name and where you work or guesses what email host you use (such as Gmail or Yahoo), they can use an email permutation tool to figure out what your email address is (thus potentially giving them the ability to hack into your accounts, send harassing messages and malware, and more).
One example of an email permutation tool is Email Permutator.
Enter your details (with your place of work or your email host as the domain) and see if your email address is listed.
Email Validators
Using an email permutation tool will give you a long list of results, which may make you think your actual email is hidden amongst the false hits.
However, by using an email validator such as MailboxValidator and entering in all of the potential email addresses a permutator comes back with, you can tell straightaway which emails are active.
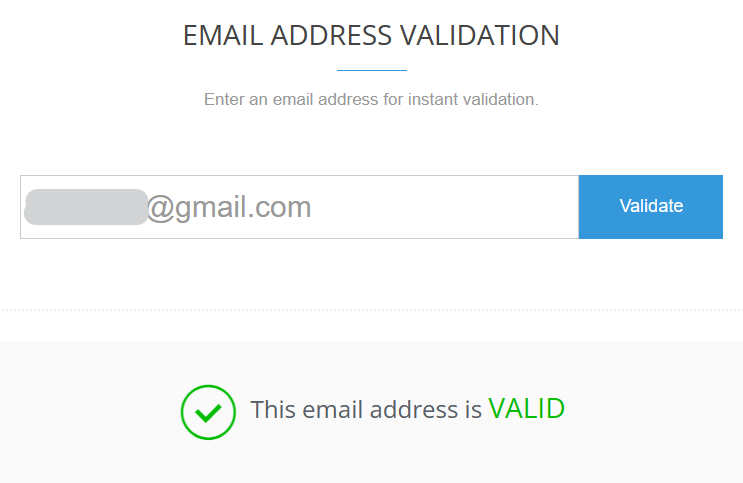
Email validators are also an easy way to test if an email listed on a people search website is still accurate.
Hacked Database Search Engines
Some of the most common forms of cybersecurity attacks are data breaches (sometimes preceded by ransomware), which occur when hackers get into a major database (such as Equifax or LinkedIn) and acquire sensitive data such as usernames and passwords, Social Security numbers, birthdates, or even bank account or credit card details before releasing it en masse online.
You can find out if your personal information has been part of a data breach by going to the HaveIBeenPwned online tool. There, you can enter your email address and see if it has been compromised and where.
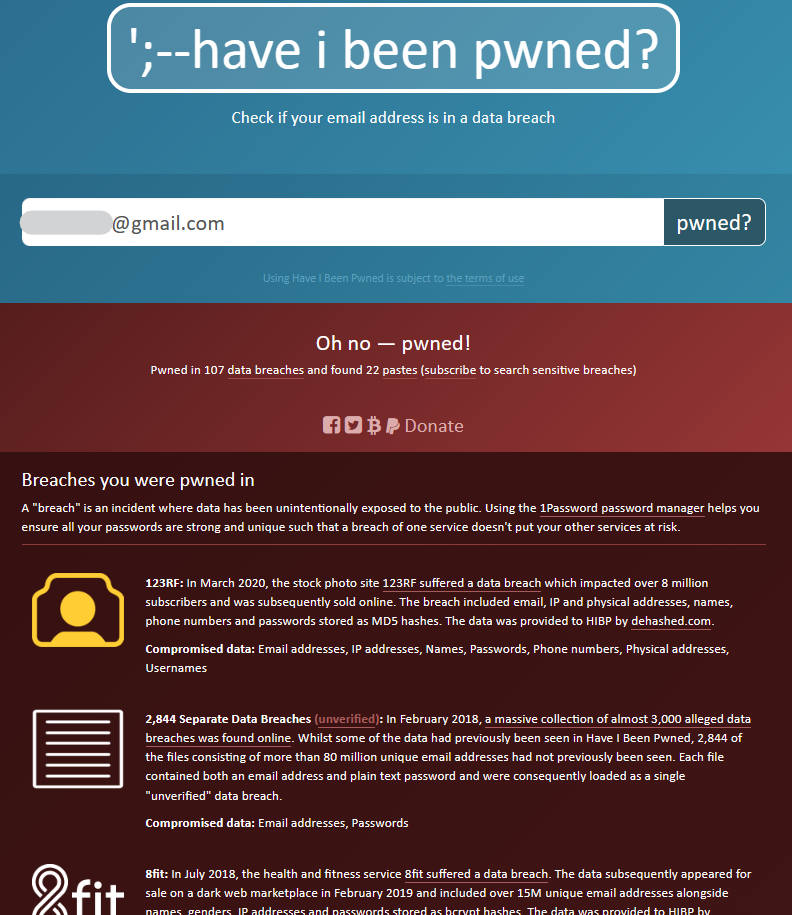
For any websites where you’ve been compromised, you should immediately change the password and repeat the step for any other website that uses the same password.
Pro tip: Don’t use the same password on multiple websites for exactly this reason. Instead, consider a password manager to generate strong, unique passwords for each of your accounts, and implement two-factor authentication to ensure your accounts stay secure.
HaveIBeenPwned also allows you to set up notifications anytime your email is part of a data breach.
Other tools include DeHashed, where you can search for variables besides your email address (such as your username or phone number), Intelligence X (which goes a step further by letting you search for your Bitcoin account number in addition to even more variables), and the Ashley Madison hacked email checker, for those with an Ashley Madison account.
Social Networks
Linking out to other social media accounts on your profiles creates an easy breadcrumb for people with malicious intent to follow.
Doxxers can easily connect your accounts to one another and find out more personal details about you.
On another note, if your personal details were shared on social media without your consent, here’s how you can report doxxing on Twitter (plus, here’s a rundown of Twitter’s doxxing policy).
Forums
Forums can be a source of personal information regardless of how much you post. If you have a forum account (such as on Reddit, a video game forum, a gardening forum, a cooking forum, etc), go to the forum, log out, and do a search using the forum’s search feature.
Most forums let you do a search using a combination of keywords. For example, you can combine your name, username, or email address with “email,” “art,” “location,” “work,” “school,” and so on. If you were doxxing yourself based on your forum account, what information could you find?
Some forum sites give you the ability to see all of the posts you’ve made. If so, review your posts and delete or edit any that include identifying information. Even seemingly harmless information like your general location (a state like New York or even America), your native language (American English, British English, Spanish, etc.), etc., can give you away.
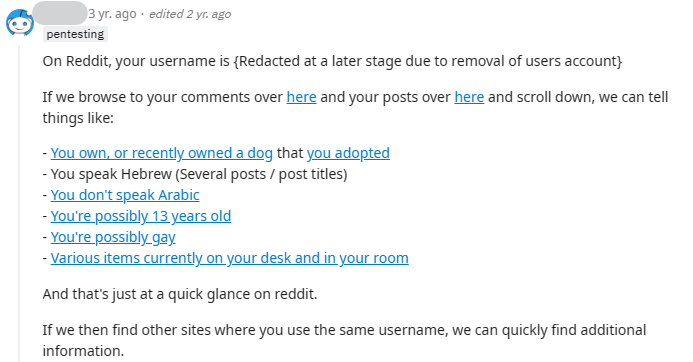
Remember: Avoid using the same avatar or profile picture across multiple forum accounts, as that makes them easy to tie together, especially through a reverse image search tool (more on this below).
Public Records
State and local governments maintain their own archives of records associated with people in their jurisdictions. This might include court records, marriage licenses, property transfers or taxes, and more.
Some government bodies and/or courthouses have online records. For example, in California, you can make a birth record request online:
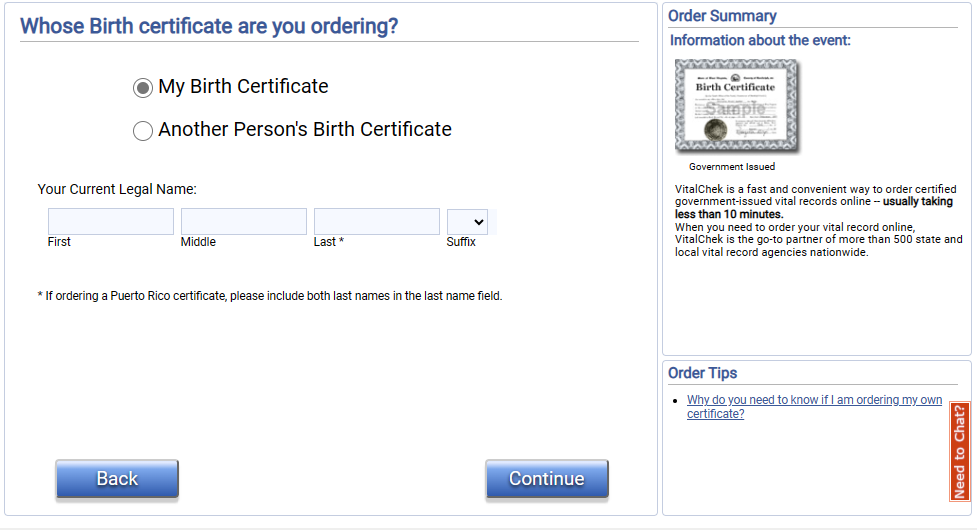
Where online public record access is not possible, the public record must be accessed in person or specifically requested. However, this isn’t difficult to do – someone could contact the state you live in pretending to be you and request your marriage certificate, for instance.
The Digital Media Project has state-specific information on accessing public records from 19 states in the US, plus the District of Columbia.
In whatever court or government record you appear, you have the option of contacting the archiving body to request that the record be made private.
You will need to justify why removing the record is necessary (typically for matters of demonstrable personal safety concerns), meaning you may need a statement from law enforcement or screenshots of harassment to back your request up.
Archives
Internet archive sites such as the Wayback Machine can be useful for viewing older versions of websites or finding sites that are no longer operational.
If you used to have a website that you shared too much sensitive information on and then later deleted, you should enter the URL into the Wayback Machine to see if any versions of it were archived.
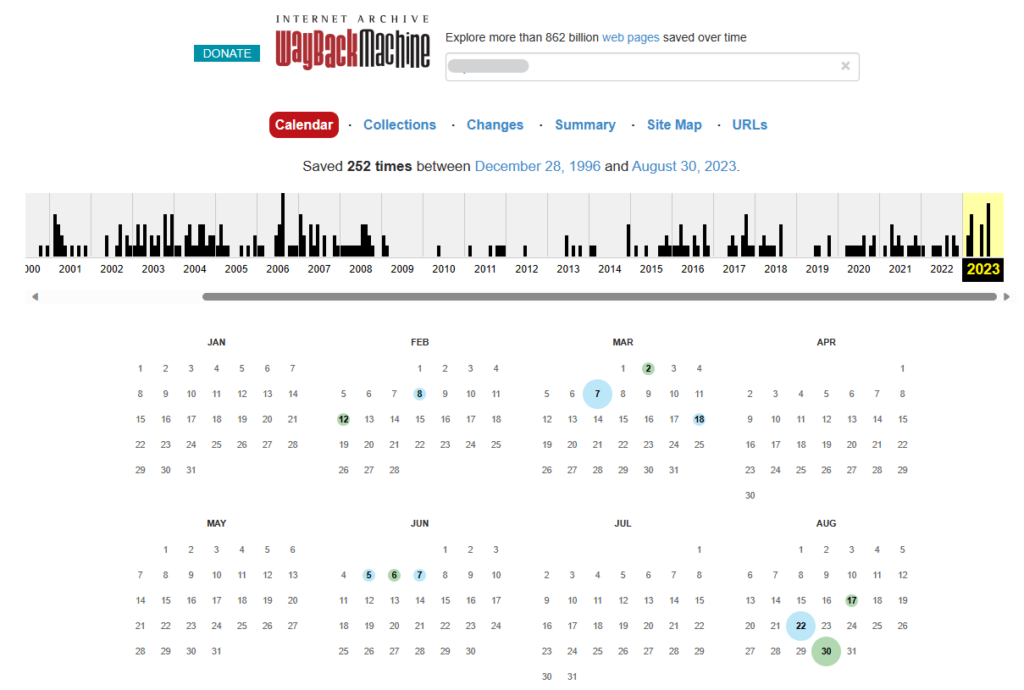
If you find your past or present website and wish for it to be removed from the Wayback Machine, follow these steps.
Whois Records
The Whois search engine enables you to type in any website and see who the owner is.
If you have a website, you should type the URL into the Whois Lookup tool to see how much of your private information is visible there. A typical record could include your phone number, home address, phone number, email, and IP address.
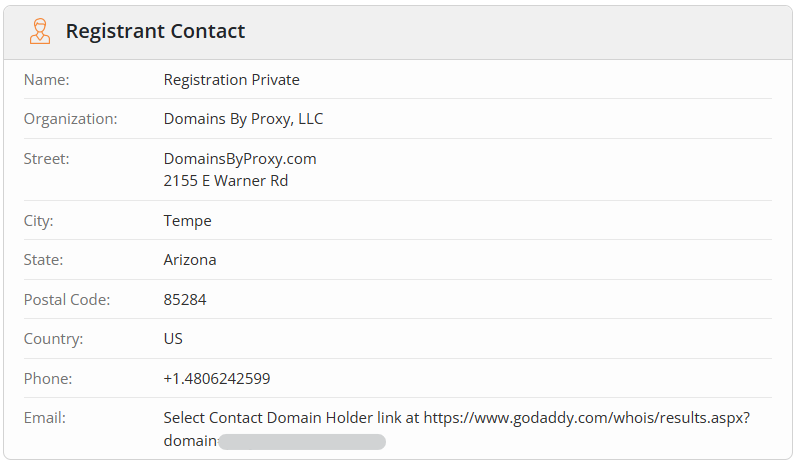
Ideally, you’ll see most, if not all, of your information removed by your domain provider – but only if you opted for private registration. If you didn’t, you should contact your registrar and update your registration as soon as possible.
Reverse Image Search
Can you dox yourself using only your face? Believe it or not, yes. Using a reverse image search tool such as Tineye, you can look for matching results across the internet to find out more information about yourself – and see how easy it would be for someone else to do the same.
To do so, find an image of yourself (such as a social media profile picture), crop out everything but your face, and then upload the image to Tineye.
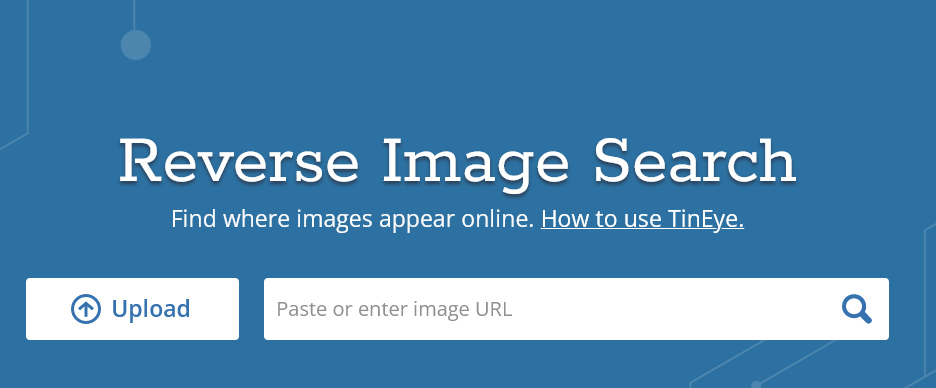
To be thorough, you should do this for each online picture you have of yourself (in the event that one connects to another or helps to unearth an old account with personal information you’d like to keep hidden).
Maps
Let’s assume you’ve uncovered your home address while doxxing yourself (a pretty easy thing to do using a people search site).
If you went to Google Maps or Bing Maps, what would you be able to see? Using street view, can you see how many neighbors you have or what buildings are nearby?
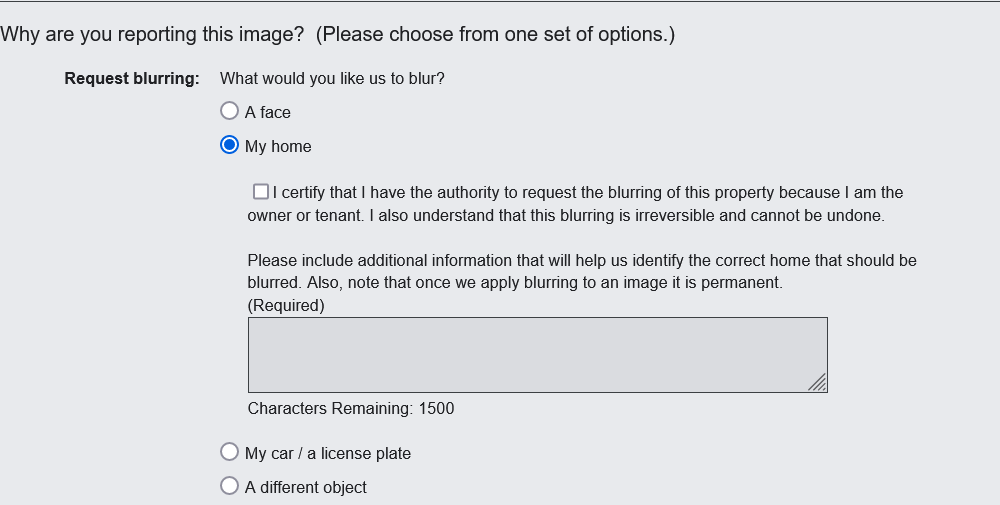
Fortunately, you can request to remove your home from Google Maps. To do so, go to Google Maps and type in your home address. Click on the Street View icon on the lower right-hand side of your screen. Once there, at the very bottom right-hand corner, you’ll see “Report a problem.”
The next screen you’ll see will give you the option of panning the image until your home (or car, or whatever you’d like to hide) is in the center of the image. From there, scroll down and select what you’d like to have blurred and why. Click “Submit” at the bottom of the page and wait a few days for results.
Become Undoxxable
The first step to becoming undoxxable is to dox yourself, which you’ve effectively done if you’ve followed each of these recommendations.
Wherever you’ve found information you’d rather keep private, be sure to take any steps you can to have the data hidden, whether it includes changing your privacy settings, sending opt-out requests, or removing your old websites from the Wayback Machine.
Each proactive step you take will reduce your digital footprint and make it much harder for someone to dox you.
DeleteMe is our premium privacy service that removes you from more than 30 data brokers like Whitepages, Spokeo, BeenVerified, plus many more.
Save 10% on DeleteMe when you use the code BLOG10.
Our privacy advisors:
- Continuously find and remove your sensitive data online
- Stop companies from selling your data – all year long
- Have removed 35M+ records of personal data from the web
Save 10% on any individual and family privacy plan with code: BLOG10












