Is Mailvelope Safe?
Laura Martisiute
Reading time: 5 minutes
Table of Contents
If you use or plan to use Mailvelope, you need to know: Is Mailvelope safe?
Below, we explain whether Mailvelope is:
- Safe to use.
- Good for privacy.
We also look at some steps you can take to improve both your safety and privacy when using this online service.
What Is Mailvelope?
Mailvelope is a free, open-source browser extension that provides end-to-end email encryption.
It uses the OpenPGP encryption standard directly within webmail interfaces like Gmail, Yahoo, and Outlook on the web.
All cryptographic keys are managed locally in the browser, with optional integration of a local GnuPG installation from version 3.0 onward.
Mailvelope can also function as a standalone encryption tool. You can use it to encrypt and decrypt files, texts, and attachments for storage on USB sticks, cloud services, and websites or to send via messaging platforms (thus avoiding metadata exposure, according to Mailvelope).
Mailvelope is available on browsers such as Edge, Firefox, and Chromium.
Is Mailvelope Safe?
Yes, Mailvelope is generally considered safe.
It provides end-to-end encryption based on the OpenPGP (Pretty Good Privacy) standard so that only the intended recipient with the correct private key can decrypt and read the message.
Mailvelope ensures that private keys are always stored and exported in an encrypted, password-protected form. This means that using a private key for decryption or signing requires both the key and its password, and even if exported, the key remains secure.
Users can enhance this security by selecting GnuPG as the encryption backend.
Because Mailvelope operates on a client-side model, the encryption and decryption of emails happen locally in the browser, meaning your private keys and decrypted messages never leave your device, reducing the risk of interception by third parties.
Mailvelope says that it has tested various threat scenarios during its professional security audits. That said, either the last security audit happened in 2019, or the company did not update its security audit page on GitHub.
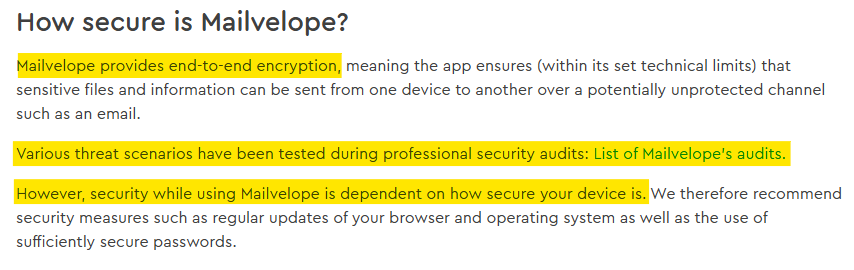
The company says that independent security audits have confirmed that Mailvelope securely isolates users’ private communications from other browser applications.
However, Mailvelope’s security depends on the browser itself.
Mailvelope is open-source, so anyone can review its code.
Mailvelope does not encrypt metadata, e.g., the subject line, email addresses, or timestamps. This means that while the body of your email remains private, certain details about the communication are still visible to email service providers and other intermediaries.
Although there have been vulnerabilities found in Mailvelope in the past, no data breaches have been associated with Mailvelope at the time of writing.
Is Mailvelope Private?
Yes, Mailvelope is generally considered private.
It provides end-to-end encryption to secure emails.
When composing an encrypted email, all data is processed locally on your computer, and only the encrypted message is sent via your webmail provider, ensuring that providers cannot read your emails.
Mailvelope only collects data using the highest standards of data minimization via Clean Insights.
During usage, 1% of users will receive a consent prompt to submit analytics data, all of which is anonymized. Mailvelope explains why and how it collects analytics data on its website.
Most internet users seem to have had a positive experience with Mailvelope.
Mailvelope outlines the kind of data it collects and why in its privacy policy. Overall, it only collects the data necessary to provide its encryption services, improve the product, and offer support while keeping most sensitive data (like PGP keys) stored locally and securely.
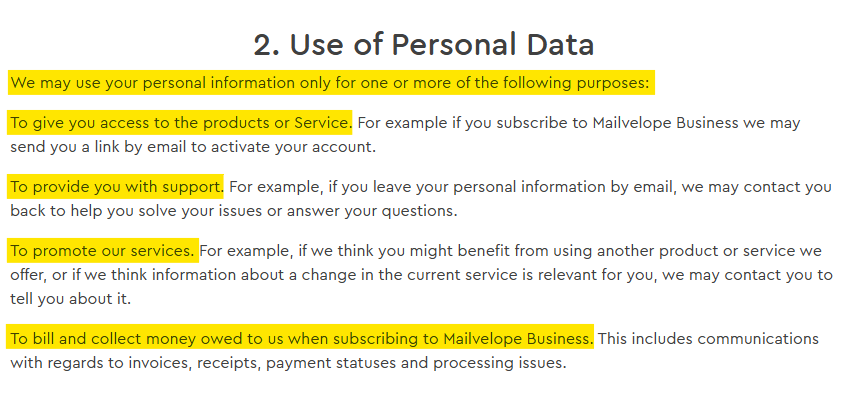
Mailvelope’s privacy policy has not been reviewed by an external privacy review site such as Terms of Service; Didn’t Read.
How to Improve Your Safety and Privacy On Mailvelope
Follow the below steps for a safer and more private experience when using Mailvelope.
- Use strong, unique passphrases for your private key. When generating your OpenPGP key pair in Mailvelope, ensure that the passphrase for your private key is strong and unique. This protects your private key from being compromised. A good passphrase should be long and include a combination of letters, numbers, and special characters. You can update your passphrase by going to Settings > Key Management in Mailvelope.
- Store your private key securely. Your private key is crucial for decrypting messages, so store it in a secure location. Avoid saving it on cloud services or unsecured devices. If possible, back it up to an encrypted external drive or secure password manager. This ensures you can recover it if needed but reduces the risk of it being stolen.
- Verify public keys before using them. When adding a recipient’s public key to your Mailvelope keyring, always verify the key through a trusted channel. You can do this by contacting the recipient directly and confirming their key fingerprint. This helps prevent “man-in-the-middle” attacks, where someone could intercept and replace a public key with a fraudulent one.
- Enable email verification using digital signatures. Mailvelope lets you digitally sign emails, which verifies your identity to recipients and ensures the message hasn’t been tampered with. To enable this, go to Compose New Email and check the box for Sign.
- Limit sharing of your public key. Only share your public key with trusted contacts or services. While public keys are meant to be distributed, limiting exposure helps prevent misuse by attackers attempting to send encrypted phishing emails or unauthorized communications in your name.
- Use private messages for sensitive communication. Even with encryption, consider using private email subjects or keeping sensitive information out of subject lines, as Mailvelope does not encrypt email metadata. Instead, place sensitive details in the body of the email, which is encrypted, and use generic or vague subject lines to avoid exposing too much information.
- Regularly update Mailvelope and your browser. Ensure that Mailvelope and your browser are always up to date with the latest versions to protect against security vulnerabilities.
Our privacy advisors:
- Continuously find and remove your sensitive data online
- Stop companies from selling your data – all year long
- Have removed 35M+ records
of personal data from the web
Save 10% on any individual and
family privacy plan
with code: BLOG10
news?
Don’t have the time?
DeleteMe is our premium privacy service that removes you from more than 750 data brokers like Whitepages, Spokeo, BeenVerified, plus many more.
Save 10% on DeleteMe when you use the code BLOG10.