What Executive Cyber Security Programs Must Include In 2025
DeleteMe
Reading time: 9 minutes

Table of Contents
If we were to give one piece of advice to organizations looking to strengthen their executive cyber security in 2025, it is to focus on personalized threats.
Lately, we’ve seen giant leaps in threat actor capabilities, including:
- Criminals using AI to create hyper-personalized phishing scams that target executives.
- Executives being targeted by deepfake scams and/or being impersonated in these scams.
- Ransomware attackers SIM swapping executives’ kids to pressure the organizations they work for into paying ransoms.
But all of these attacks have one (very low-tech) input in common: executives’ professional and personal information.
Taking executive information offline reduces criminals’ ability to target executives (and other employees within your organization) with even the most sophisticated attacks.
6 Executive Cybersecurity Risks Fuelled By Executives’ Personal Data
Criminals use executives’ professional and personal data to carry out the following attacks.
Executive phishing
Executive phishing attacks are highly personalized to the target, i.e., the executive. This makes these kinds of phishing scams very difficult to spot.
Like most social engineering attacks, executive phishing typically involves four steps:
- Information gathering
- Relationship development
- Exploitation
- Execution.
The information-gathering step is probably one of the most important.
Here, hackers determine who to attack, who their target is likely to share information with, and under what pretext.
We know from leaked criminal chat transcripts that attackers use open-source intelligence tools like data brokers to find targets and individuals to “name drop” within their social engineering campaigns to make them look more legitimate and more likely to succeed.
We also know that AI is making executive phishing faster and easier.
Harvard researchers found that AI models can gather accurate and useful data on people in 88% of cases.
AI can also help create convincing executive phishing messages. Those same Harvard researchers saw AI-generated phishing emails get a 54% click-through rate – the same as emails crafted by humans and much, much higher than arbitrary phishing emails (12% click-through rate).
Personal information needed for executive phishing: Varied, including contact details, education and employment history, company org chart, family member details, and more.
CEO fraud
In CEO fraud attacks, threat actors pretend to be senior executives or board members to other business leaders, VIPS, or employees.
Cybercriminals’ goal in CEO fraud is usually to get the recipient to make an unauthorized financial transfer. Sometimes, they’ll attempt to con the recipient into disclosing sensitive data or downloading malicious files instead.
CEO fraud happens like any other social engineering attack, with the likelihood of success depending heavily on the reconnaissance stage.
However, unlike spear phishing attacks, where criminals can impersonate professional and personal contacts, CEO fraud emails tend to come from C-suite executives, like the CEO or CISO.
That’s why, in these attacks, threat actors need to understand the org chart of their target company. This is easier than you might think, thanks to B2B data brokers (more on them below) that provide this information to anyone looking for it.
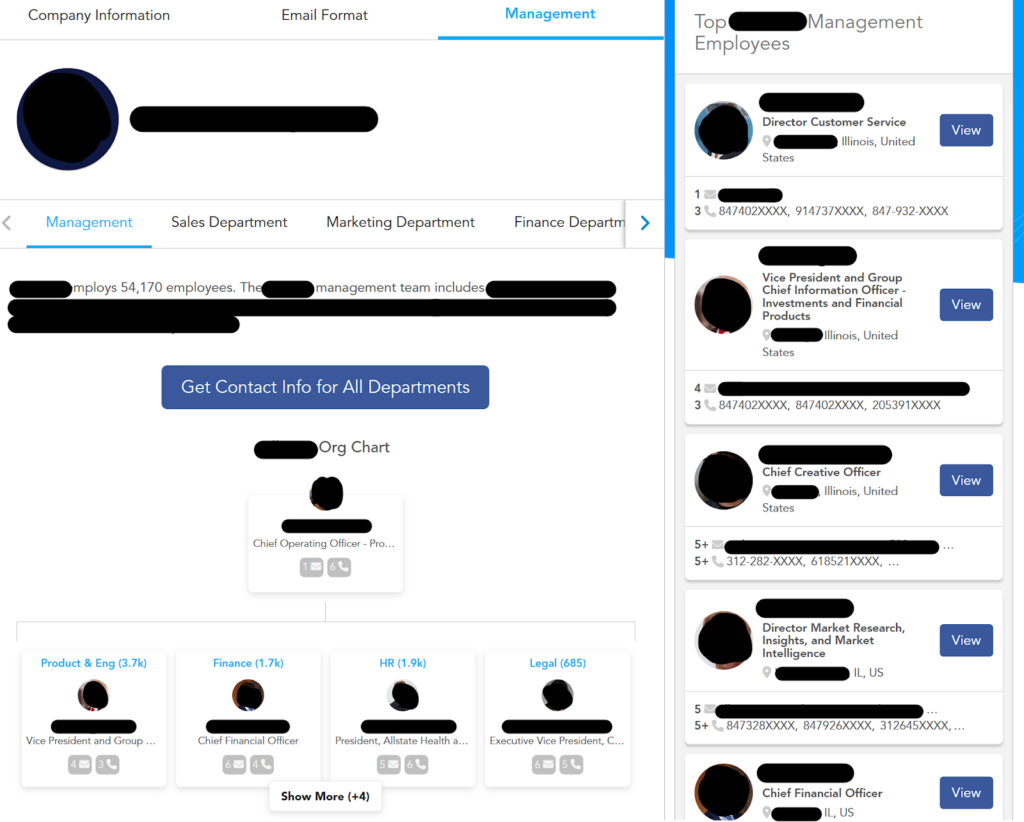
Information needed for CEO fraud: Varied, but success hinges on finding up-to-date business org charts.
Account takeover
Account takeover is an attack where threat actors take ownership of executive online accounts.
Rather than relying solely on data breaches, cybercriminals also use personal information available on the internet to guess passwords, especially for high-value and high-profile targets like corporate executives.
Targeting people like this is time-consuming but often pays off.
The reason why is that many people use personal information, like a family member’s name or the city they were born in, for their credentials.
For example:
- Nearly 25% of executives use their birthday in their password.
- 11% of breached executive passwords contain company-related strings.
- Another 11% contain the account holder’s name or surname.
Personal information needed for executive account takeover: As varied as possible, including family member names, addresses, etc.
SIM swap attacks
And more recently, SIM swapping executives’ kids to pressure the executives into paying ransoms.

Cybersecurity researchers noted cases where criminals SIM-swapped the phones of executives’ children, then called the executives from the kids’ phone numbers to intimidate them.
As Charles Carmakal, CTO of the cybersecurity company and subsidiary of Google, said during a Google Security Threat Intelligence Panel at the 2024 RSA Conference:
“Think about the psychological dilemma that the executive goes through – seeing a phone call from the children, picking up the phone and hearing that it’s somebody else’s voice? Sometimes, it’s caller ID spoofing. Other times, we see demonstrated SIM swapping family members.”
Personal information needed for SIM swap attacks: Varied, but includes executives and their children’s phone numbers.
Deepfake scams
If it sounds like your boss and looks like your boss, then it must be them, right? With deepfake scams on the rise, that’s no longer the case.
Deepfake scams are when criminals collect audio and visual samples (e.g., executive voice recordings or footage of their faces) of people known to their targets and feed this data into AI models.
They end up with phony audio or video that mimics a person’s likeness or speech patterns known to their victim.
LastPass recently experienced a deepfake scam that tried to impersonate the company’s CEO.
The attackers used WhatsApp calls, texts, and voice messages (all generated by AI) to create a sense of urgency and push the targeted employee into action.
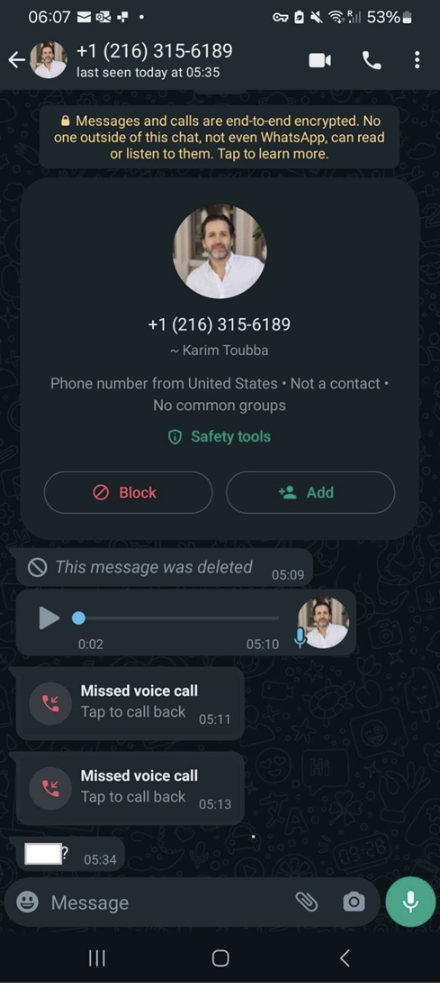
Luckily, the employee noticed the unusual communication channel and other signs of social engineering (e.g., the fake urgency) and alerted LastPass’s internal security team.
The number of companies (and executives) who have been targeted with deepfake scams is seriously concerning.
Personal information needed for deepfake scams: Contact details, company org chart, and audio or video clips of the individual to be impersonated.
Fake ransom letters sent to executives’ homes
Criminals never stop innovating.
A new scam is targeting U.S. executives by sending ransom letters to their home and business addresses, falsely claiming to be from a particular ransomware group.
Because there’s no evidence of data exfiltration or any standard ransom negotiation channel, these letters are believed to rely purely on fear rather than any actual compromise of company systems.
Similarly, in the past, there have been reports of ransomware groups approaching employees, including executives, directly to assist in planning ransomware attacks.
Personal information needed for ransomware-related attacks: Business and home addresses, company org chart.
Scrubbing Executives’ Personal Data from Common Information Exposure Sources
It’s not hard for criminals to find executives’ professional and personal information.
From social media profiles such as LinkedIn to corporate websites and press releases, attackers have a ton of resources for gathering intelligence on their targets.
One of their favorites has to be data brokers and people search sites.
Data brokers and people search sites are companies that collate people’s personal information into a single place. Their customers are mostly marketers who want to better tailor their ads. However, there is little to prevent cybercriminals from accessing personal information on data brokers as well.
Data broker profiles pose a threat to executive cybersecurity because they:
- Are easy to find with a quick Google search and are among the first few results shown.
- Include a lot of personal information, like names, phone numbers, email addresses, employment history, and more. The data available on these profiles is only getting more detailed and is being pulled from sources as varied as public records, social media accounts, breached datasets from the dark web, and more.
- Are cheap or even completely free to access.
Removing executive information from data broker sources is an important part of executive protection. It is also a simple step organizations can take to minimize the risk that their executives will fall victim to a cyber attack.
Status Quo Executive Cybersecurity is Not Good Enough in 2025
Executive security protection typically consists of two layers:
- Executive security training.
- Technical controls like antivirus solutions.
The first of these is very failure-prone. Busy executives don’t always have the time to attend security awareness training sessions.
And even when they do, research shows that security training is quickly forgotten unless it happens continuously. According to the nonprofit USENIX, six months after a phishing training session, individuals show no marked improvement in being able to distinguish between a legitimate and a phishing email.
The second layer – technical controls – is meant to catch and remediate cyber risks like malware. They can’t be relied on, either. Often, the threat isn’t a malicious attachment or executable; it’s the contents of an email or voice note and the actions that happen as a result.
Phishing emails that don’t contain malicious links or files can circumvent email security filters; “multi-factor authentication fatigue attacks,” where cybercriminals flood a target’s app with push notifications, can trick executives into authenticating fraudulent login attempts; threats use obfuscation techniques to bypass antivirus and endpoint protection services and tools.
Digital risk protection for executives requires another layer of defense – information removal.
Executive Cyber Security Protection with Data Broker Removal
Data brokers are an important reconnaissance tool for threat actors and one of the reasons why personalized attacks have become so frequent.
Monitoring for and removing executive personal information from data exposure sources won’t completely isolate business leaders from cyber threats. However, doing so will make it harder for cybercriminals to conduct open-source intelligence and will reduce the number of opportunities for exploitation.
- Employees, Executives, and Board Members complete a quick signup
- DeleteMe scans for exposed personal information
Opt-out and removal requests begin - Initial privacy report shared and ongoing reporting initiated
- DeleteMe provides continuous privacy protection and service all year
DeleteMe is built for organizations that want to decrease their risk from vulnerabilities ranging from executive threats to cybersecurity risks.
Want more privacy
news?

Is employee personal data creating risk for your business?

















