Executive Reputation Management: How Data Broker Profiles Create Reputational Risk
Table of Contents
There’s no shortage of executive reputation management strategies. Some popular ones include thought leadership, monitoring online reviews, search engine optimization (SEO), and maintaining an active social media presence.
However, another important part of executive online reputation management is data broker removal.
Data brokers collect information about executives and then sell this data to third parties like marketers. Because few data brokers do customer vetting, executive personal information can also end up in the hands of bad actors such as cybercriminals or disgruntled customers.
Hard to remove and difficult to keep on top of, data broker profiles expose your company’s executives and thought leaders to a host of threats that can ruin their good reputation.
This short guide explains why data broker opt-outs are essential to executive and CEO reputation management services and why removing upper management data from online sources can help preserve executives’ online image and their companies’ reputations.
4 Ways Data Brokers Increase Executives’ Reputational Risk
Personal information about executives on data broker sources exposes upper management to four types of risk: Cyber attacks, impersonations, mistaken identity, and harassment.
All can have a significant impact on executives’ personal brand and public persona and cause serious harm to their and their organizations’ positive reputations.
Data broker opt-outs help your business maintain favorable executive and brand reputation and control the online narrative.
Cyber attacks
What: Cyber incidents, especially ones that compromise customers’ data.
How: C-suite executives are often the ones who enable cyber attacks in the first place.
This is because:
- Executives have high levels of access. This makes business leaders an attractive target for threat actors.
- Executives are highly visible. Due to their high profile, it’s easy for hackers to find personal information about corporate leaders through online sources like data brokers. They can then use this personal data to guess passwords and security questions, personalize phishing emails, and conduct MFA fatigue attacks.
- Executives frequently sacrifice security for convenience. C-level executives admit to circumventing security protocols if they’re in a rush.
For example, the aerospace and defense company FACC’s CEO was fired immediately after a threat actor impersonated them to socially engineer a finance employee into making a 50 million euro transfer.
While FACC did not share details of what the phishing email looked like, the threat actor likely personalized it with information found through online sources.
Impact on executive reputation: When a company falls victim to a cyber attack, customers rarely blame the cybercriminals responsible for the attack. More often, they blame C-level executives like the chief executive officer (CEO).
With devastating attacks happening almost daily, Americans expect businesses to take cyber risk seriously. Customers are unforgiving when they find out that their data was compromised.
After a breach, negative publicity (including negative reviews on review sites, social media comments, and other negative content) is the norm. For business executives, the resulting negative press can be hard to shake.
Impersonations
What: Fake executive accounts on social media platforms (i.e., LinkedIn, Facebook, etc.) and/or emails to clients/vendors that seem to come from an executive but are actually from a threat actor.
How: All a cybercriminal needs to create social media accounts in an executive’s name or write fraudulent emails to clients, vendors, and other third parties is an executive’s personal information.
For example, email address, phone number, and employment history. This data is available with a simple Google search, most commonly via data broker websites.
Perhaps unsurprisingly, executive impersonations are on an upward trajectory.
Impact on executive reputation: Executive impersonations negatively affect an executive’s corporate reputation. They can mislead customers and vendors and influence the public’s opinion about an executive and the company they work for.
Mistaken identity incidents
What: When someone believes that an executive is someone else.
How: Data broker negligence. There are two key ways executive misidentification happens.
The first and most common one is erroneous background checks.
Prospective employers often perform background checks using data broker sources. However, because data brokers are error-prone, an executive’s profile may include incorrect information. This can cost an executive a job.

The second is internet vigilantism.
It has become increasingly common for the general public to take “justice” into their own hands via methods like internet sleuthing and doxxing.
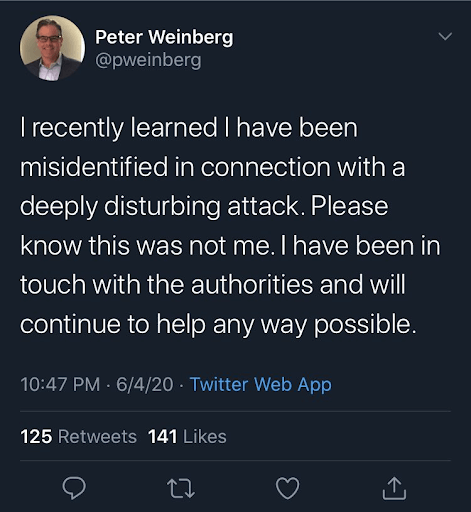
Finance marketing executive Peter Weinberg experienced this first-hand when online vigilantes misidentified him as someone who had physically attacked children and adults on a trail that Weinberg regularly cycled.
After the local law enforcement shared the wrong date for when this incident happened, internet vigilantes conducted open-source intelligence and decided that Weinberg was the man in question.
Weinberg then started to receive threatening messages like “Nice job assaulting a small child today. You need to be fired from your job immediately” and “You deserve to pay.”
He was doxxed, and his home address was publicly shared.
Impact on reputation: When an executive is mistaken for someone else, their reputation can be damaged through no fault of their own. Business reputation can also suffer as a result.
Harassment
What: Details from an executive’s personal life or past being used against them.
How: As data broker profiles become more detailed, third parties have access to more and more of executives’ personal information.
In addition to basic data points like email addresses and phone numbers, bad actors (ex-employees, co-workers, activists, etc.) can now find out information about an executive’s family relationships, political affiliations, donations, and more.
Impact on reputation: Depending on how sensitive the information a threat actor can find is (like if an executive is donating to a controversial cause or their spouse or kids have attended a controversial rally), this could cause serious damage to an executive’s and their company’s reputation.
For example, the former CEO of a popular web browser had to resign after just two weeks of being appointed for the role. The reason? It came to light that several years prior, he had donated in support of a controversial ballot initiative and contributions to fringe Republican candidates.
In this case, the ex-CEO’s reputation was damaged to the point where his personal actions were being held against him years later, even impacting the reputation of a company he co-founded.
According to research by the New York-based public relations firm Weber Shandwick, a company’s and its executives’ reputation can also have a substantial effect on a company’s market value and bottom line. Besides impacting profitability, a reputation crisis can result in strained stakeholder relationships and negative company culture (including lower employee retention).
Executive Reputation Management vs. DeleteMe
An executive’s online presence is made up of more than just news articles, forum discussions, tweets, and their company’s digital marketing initiatives.
With personal information easily accessible via data brokers, anyone can find out sensitive details about an executive’s life and then use that information to cause reputational damage, either directly (i.e., by sharing controversial information publicly) or indirectly (i.e., through a cyber attack or impersonation incident).
Executives and their teams must consider all the ways that bad actors could harm their reputations to avoid having to subcontract a crisis management team.
DeleteMe removes executive data from data broker sources, making it more difficult for threat actors to use personal information in attacks against business leaders.
- Employees, Executives, and Board Members complete a quick signup
- DeleteMe scans for exposed personal information
- Opt-out and removal requests begin
- Initial privacy report shared and ongoing reporting initiated
- DeleteMe provides continuous privacy protection and service all year
DeleteMe is built for organizations that want to decrease their risk from vulnerabilities ranging from executive threats to cybersecurity risks.












