Preventing Executive Phishing In 2025
DeleteMe
Reading time: 12 minutes

Table of Contents
Executive phishing is one of the biggest threats your organization faces in 2025 and beyond.
From studies published during the past year, we know that phishing remains a top threat vector. We also know that executives (CEOs, CFOs, etc.) are four times more likely to fall for phishing than the average employee.
A compromised executive account (which often has advanced permissions) gives a threat actor direct access to the heart of your organization’s IT environment, while a compromised executive who thinks they are talking to a colleague or superior can wipe out millions of dollars of enterprise value in minutes by accidentally (or otherwise) making a fraudulent payment or enabling a data breach.
Fortunately, at DeleteMe, we know a lot about preventing executive phishing.
Since 2012, DeleteMe has helped dozens of household name companies protect their executives from phishing attacks by taking their personal information away from sources of online exposure.
Information removal is a tried and tested method of executive phishing risk reduction that still works extremely well today
- DeleteMe removes executives’ personal data from online data exposure sources.
This article distills our experience and recent market data into a concise guide to preventing executive phishing.
Executive Phishing Definitions
Phishing executives is “executive phishing.”
Phishing = A type of cyber attack where criminals pretend to be someone else (e.g., a colleague, bank, service, etc.) to trick people into taking specific actions or sharing sensitive information (e.g., login credentials or personal details). Phishing campaigns are often broadly targeted. For example, a phishing email might be sent to everyone in a company.
Executive phishing = Phishing campaigns targeted at executives, including emails, texts, social media messages, phone calls, and lately, even video calls.
The term “executive phishing” is also sometimes used to refer to phishing attacks that impersonate executives to other employees (more appropriately known as “CEO email scam,” “CEO fraud,” or “whaling.”)
Below is a table with different executive phishing definitions and examples.
| Term | Description | Examples |
| Phishing | Broad attacks pretending to be trusted sources that aim to steal info or trick users into actions. | 2024 Midnight Blizzard campaign that targeted 100s of companies in the US. |
| Executive Phishing | Phishing aimed at executives via email, texts, calls, social messages, or videos. | 2024 attack on the CEO of global advertising firm WPP that used a voice clone and a fake WhatsApp account. |
| Whaling | Phishing that targets high-level execs (“whales”), often impersonating them to others. | 2024 attack on a campaign official in a US presidential campaign. |
| Executive Spear Phishing | Highly targeted, personalized phishing aimed at a specific executive. | 2015 attack on Mattel, where a fake email from the “new CEO” led to a $3M wire transfer. |
| Executive Cell Phishing | Phishing that either targets executives or impersonates them to other employees via mobile phones (work or personal). | 2024 attack on a Ferrari executive that impersonated the company’s CEO. |
Executive Phishing vs Whaling
Executive phishing and whaling mean more or less the same thing.
- Executive phishing is phishing carried out against executives.
- Whaling is phishing carried out against high-ranking executives, i.e., the “whales.” In these attacks, criminals often impersonate executives to other employees, hoping they won’t question the phishing attempt due to the impersonated person’s authority. This is also known as “CEO email scam” or “CEO fraud.”
An example of a whaling attack is the 2024 attack on a high-level staffer in the presidential campaign. The attack resulted in the leak of sensitive documents.
There are lots of older examples too, like the attack on Snapchat’s payroll department involving an email that looked like it came from the company’s CEO (Evan Spiegel), asking for current and former employees’ payroll information.

Believing the email to be legitimate, the employee complied with the request. The result? Multiple employees’ personal information was shared with criminals.
Executive Spear Phishing
Executive spear phishing is a subset of spear phishing, which is a targeted phishing attack that’s tailored to a specific role or person. Executive spear phishing is a phishing attack that’s explicitly tailored and personalized to an executive.
For example, in 2015, a finance executive at the toymaker Mattel received an email pretending to be from the new CEO, urgently requesting a wire transfer to a new vendor in China. The executive thought the request was real and performed a $3 million transfer to a Chinese bank account.
The fraud was only discovered after the executive mentioned the payment to the real CEO, who denied ever authorizing it.
Fortunately for Mattel, the next day after the transfer, there was a bank holiday in China, which delayed the funds and led to Mattel recovering the entire $3 million.
Executive Cell Phone Phishing Scams
Executive cell phone phishing scams are also on the rise, with cybersecurity researchers warning to watch out for mobile phishing threats.
It is an attack that targets executives via their work or personal mobile phones.
Executives either receive calls (an attack known as “vishing”) from criminals or receive fake messages (known as “smishing”) meant to manipulate them into revealing confidential information or doing something that will compromise the security of an organization.
Phishing Email Training for Executives
Phishing email training for executives is important, but training won’t stop executive phishing attacks.
In general, phishing and security awareness training isn’t something that most employees are thrilled about. Executives, who have busy schedules, are no exception.
- Of employees who receive security awareness training, one in five (22%) admit they would rather be stuck in rush-hour traffic than attend it.
- One in ten (11%) of those receiving security awareness training say they would prefer a root canal.
Phishing email training is not effective against the personalized phishing campaigns that tend to target executives.
Executive Phishing Personal Data
Personal information plays a key role in executive phishing attacks.
By personalizing their phishing campaigns with executives’ personal details, attackers can create very targeted, customized messages that are more believable and more likely to succeed.
Take a look at the following executive phishing email.
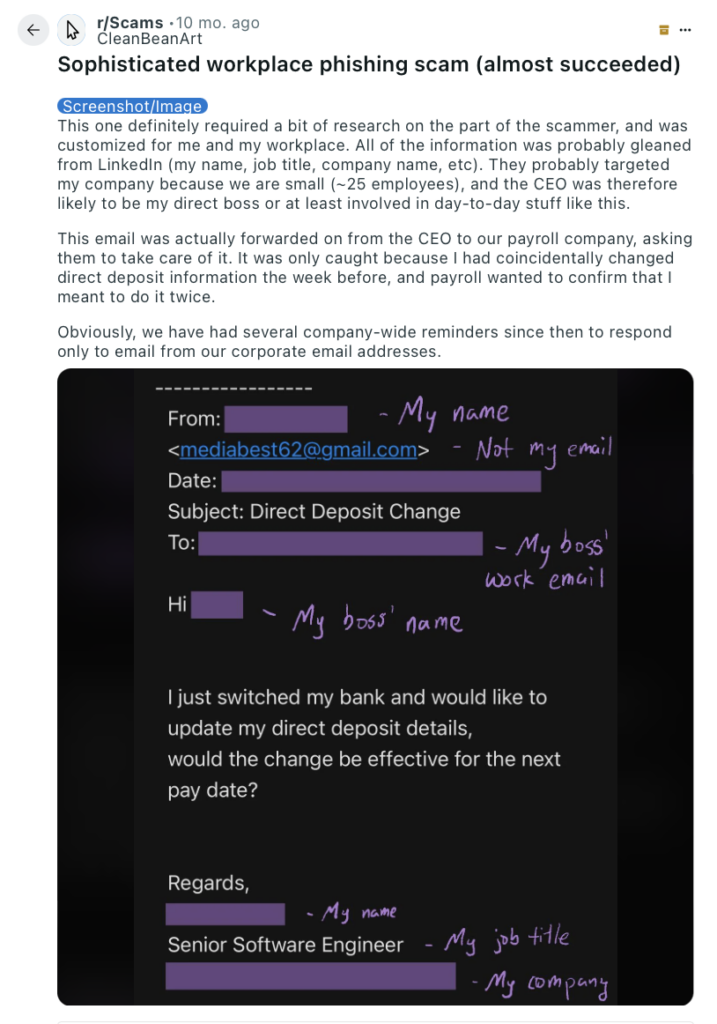
The attacker impersonated a senior software engineer to the company’s CEO, asking them to change their direct deposit details.
Note how the attacker knew and used:
- The software engineer’s name and role.
- The company name.
- Their boss’ name.
- Their boss’ work email.
The only red flag was the sender’s email address.
Attackers find executives’ details through information on:
- Social media profiles (e.g., LinkedIn, Facebook, etc.).
- Corporate websites (great for finding information on executives’ roles and responsibilities).
- News articles, press releases, interviews, and conference speaker bios.
And… data brokers.
Data brokers are a particularly dangerous source of executive personal information exposure. These companies collate executives’ details from multiple different sources into one place, making reconnaissance much easier and faster.
Rather than having to piece bits of information from various different sources themselves (social media, public records, past data breaches, etc.), attackers can get it all in one place through data brokers.
Unfortunately, the role that data brokers play in executive phishing attacks (and cybersecurity threats in general) is rarely talked about.
To minimize executive phishing threats, it’s more common to recommend security awareness training, email phishing protection solutions, and multi-factor authentication (MFA).
While relevant and necessary, these controls can’t stop personalized attacks.
Data broker removal services can prevent executive phishing by making it harder for attackers to launch personalized attacks.
How Data Brokers Make Executive Phishing Easier
Executive phishing involves three steps: finding a high-profile target, researching the target, and creating the bait.
Data brokers make each one of these steps easy.
Here’s how data brokers enable each one of these three executive phishing steps:
1. Finding a high-profile target
Like any other spear phishing attack, executive phishing attacks start with cybercriminals finding specific individuals to phish.
How does this happen? Well, thanks to a series of document leaks from a prominent cybercriminal group, we know that threat actors use business data brokers to find potential targets’ names, job roles, and contact information (email addresses, phone numbers, etc.).
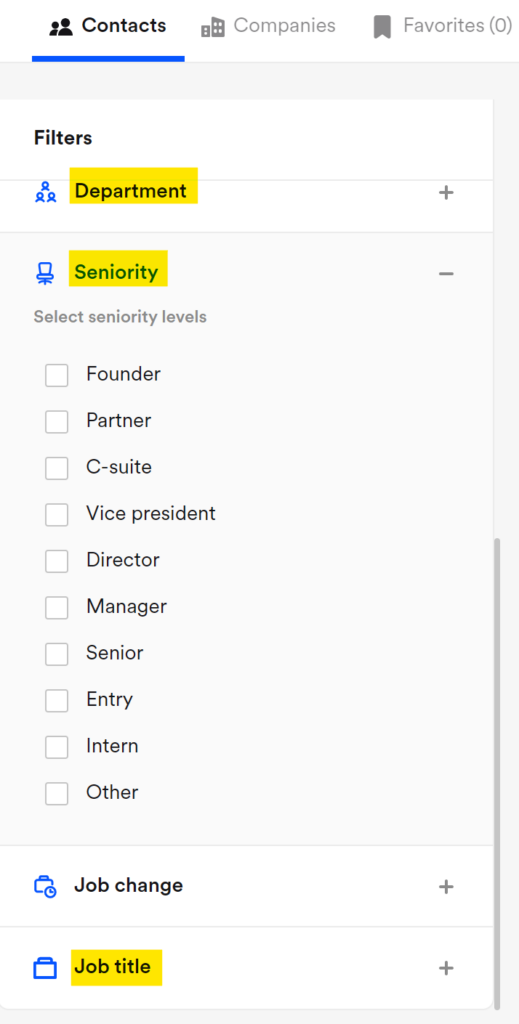
These kinds of business data brokers are valuable because they provide lists of employees, including C-suite ones, for thousands of companies worldwide.
On most B2B brokers, you can even filter employees by department and seniority:
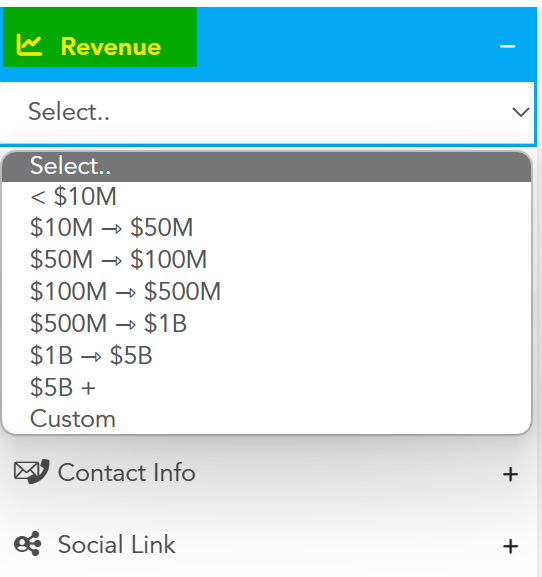
Other filtering options provided are organizations’ financial data, i.e., reported revenues. This is a handy feature for financially-motivated attackers:
2. Researching the target
Once attackers identify a target, they start their research. Here’s the kind of information they can find about executives on data broker databases:
Work experience and education
The profiles that business data brokers have on employees include a ton of exploitable information, like their work experience and education.
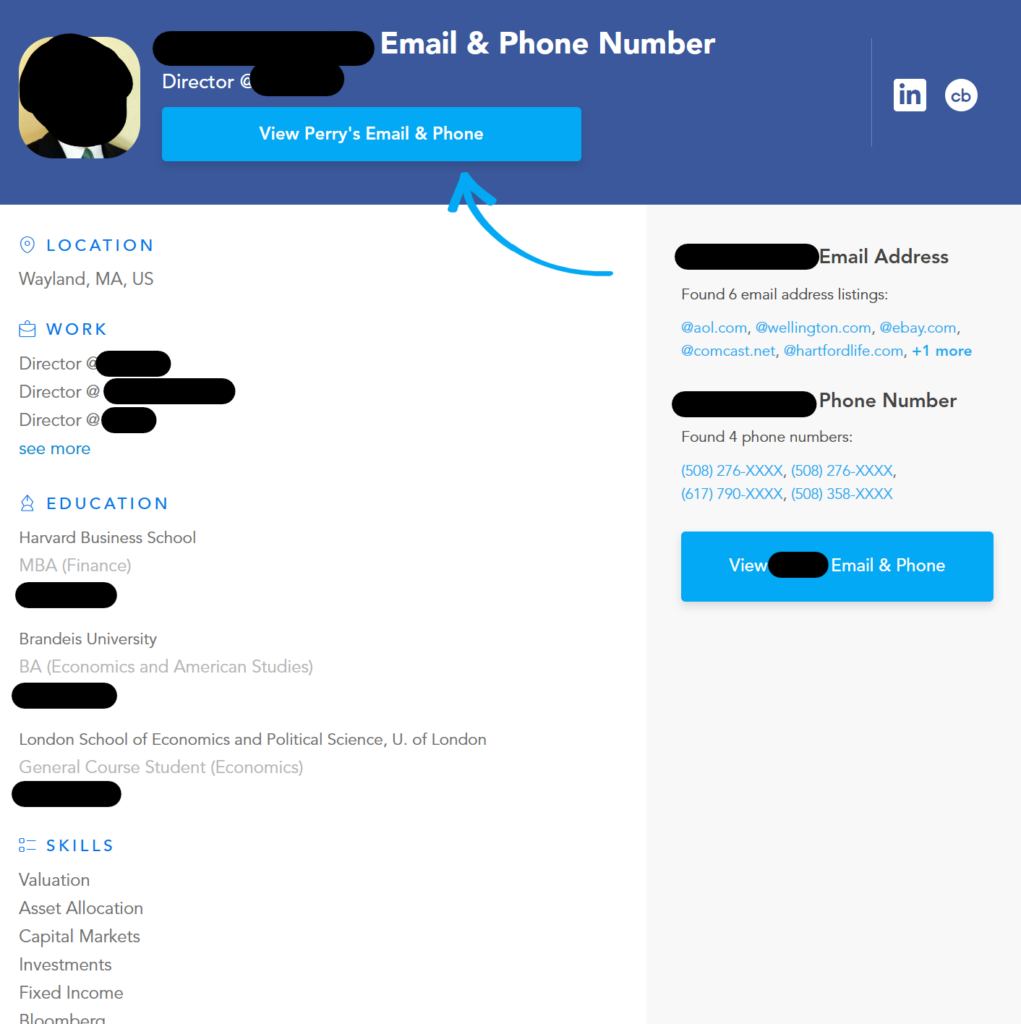
Knowing where an executive went to school and where they worked previously can help threat actors find a “hook” for executive phishing campaigns.
Business org chart
Some business data brokers also show org charts for companies and employees, including for specific departments:
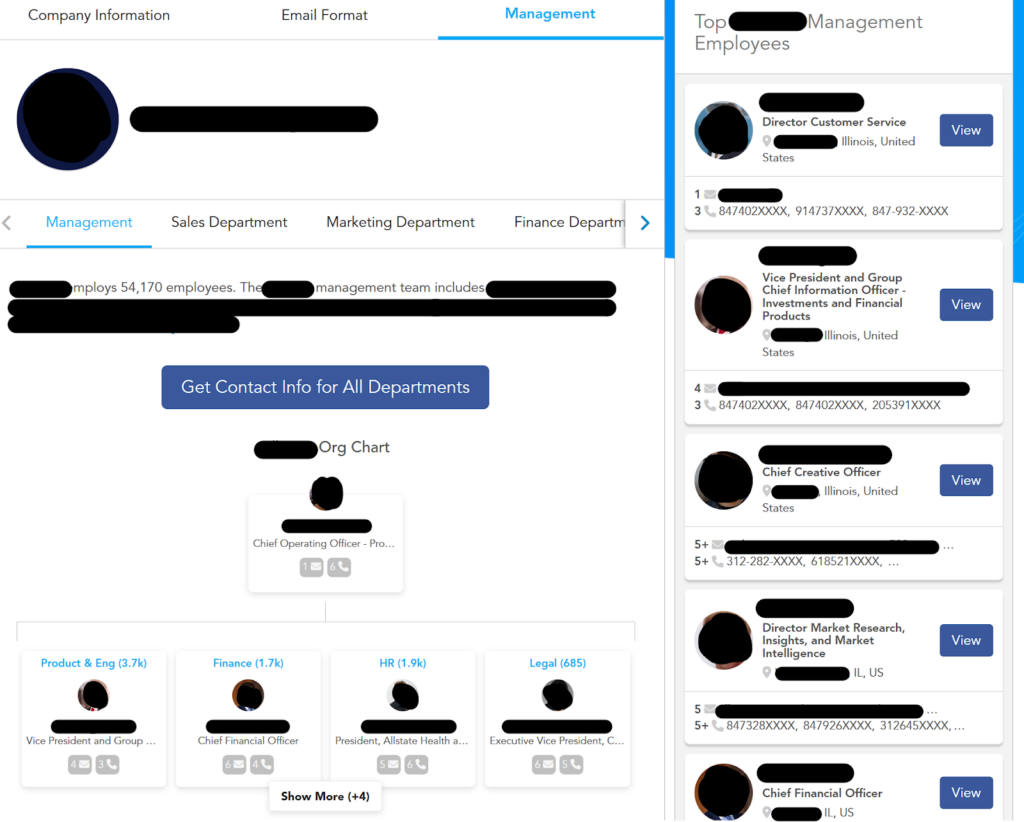
Why does this matter?
For an executive phishing attack to succeed, there needs to be a justifiable and valid context between the sender and the recipient.
For this reason, executive phishing attacks that target C-level executives often seem like they come from other high-level employees. Knowing a company’s internal structure makes it easier for scammers to choose the right individuals to impersonate.
Communication style
Business data broker profiles also include links to executives’ social media pages like LinkedIn and Facebook. These often include other relevant information that threat actors can use to make their executive phishing campaigns look more believable.

For example, executives’ social media posts and comments can give attackers an indication of the executive’s tone of voice.
Threat actors can then match the language in their email to the language the executive likely uses.
Today, criminals don’t even have to do this manually. Instead, they can provide a sample of an executive’s communications to AI chatbots to create a message in their writing style, saving time and cutting down on potential mistakes.
Family members
Cybercriminals are not limited to professional data when it comes to information gathering.
In addition to business data brokers, there are also “regular” data brokers, commonly known as people search sites. These data brokers have more sensitive data about individuals, including details about their family members and marital status.
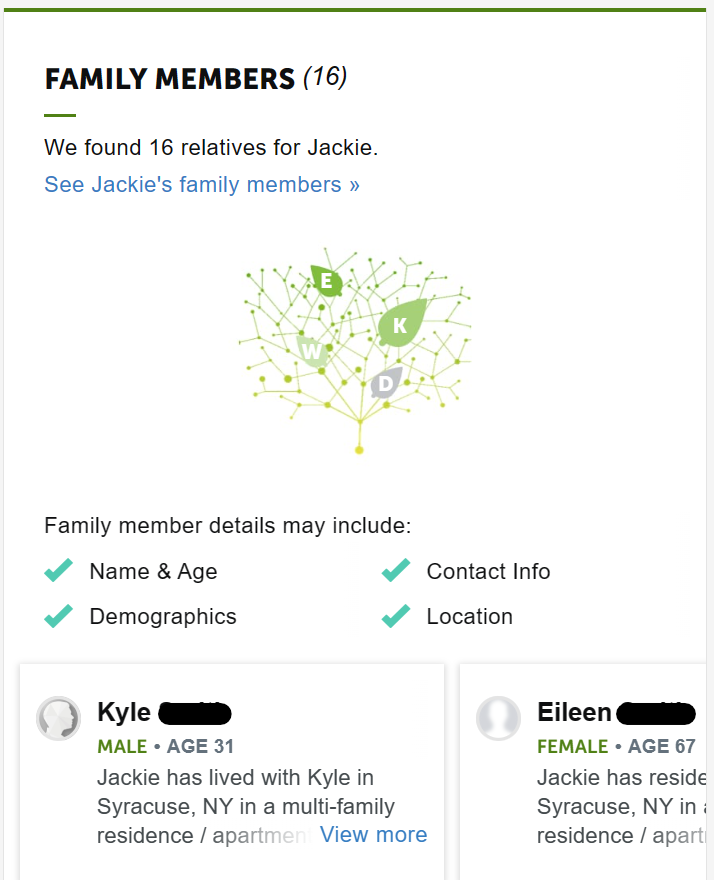
Depending on the context of the phishing email, it might make sense for cybercriminals to include this information as proof that they are trustworthy.
Social profiles
Some data brokers also include links to people’s professional and personal social media profiles like LinkedIn, Facebook, Instagram, etc.

Based on the kind of information executives share on their social accounts, this could give cybercriminals even more data to play with.
3. Creating the bait
When a threat actor gathers enough personal information about their target, they can use social engineering tactics to create a convincing executive phishing campaign.
This can come in the form of a phishing email, phone call, or social media/text message.
Whatever a cybercriminal’s goal—tricking the executive into handing over sensitive data (login credentials, bank account or credit card details, etc.), deploying malware (for example, ransomware), or authorizing a fraudulent wire transfer—they are likely to succeed.
That is, as long as they have thoroughly researched their target and picked a trusted person to imitate.
More than one in three business leaders say they have clicked on a phishing link.
AI-Generated Phishing Scams Increasingly Target Corporate Executives
AI is making executive phishing faster and more effective.
Criminals are using AI to:
- Find and analyze large amounts of publicly available data about executives and the organizations they work for. This dramatically decreases the amount of time it takes to build a detailed target profile. A Harvard study found that AI models can collect accurate and useful data on individuals in 88% of cases.
- Identify details, like a target executive’s writing style or network of colleagues, which allows them to personalize messages with context that would be difficult to piece together manually. We know from leaked criminal chat transcripts that attackers look for contacts to “name drop” within their phishing campaigns to make them look more believable.
- Translate phishing messages into the executive’s native language, improving credibility and imbue messages with local cultural references. That same Harvard study quoted above found that AI-generated phishing emails saw a 54% click-through rate – the same as emails written by humans and higher than arbitrary phishing emails (12% click-through rate).
In other words, AI has turned what used to be highly tailored, one-off phishing campaigns (i.e., the very definition of executive phishing) into attacks that can be done at scale.
Executives everywhere are feeling the brunt, including at large enterprises.

E-commerce group eBay and British insurer Beazley have noted a rise in executive phishing campaigns that include personal information, more than likely obtained via AI analysis of online data.
“This [executive phishing] is getting worse and it’s getting very personal, and this is why we suspect AI is behind a lot of it. We’re starting to see very targeted attacks that have scraped an immense amount of information about a person,” said Kirsty Kelly, Beazley’s chief information security officer, in a Financial Times article.
Executive Phishing Prevention Requires Executive Data Removal from Common Information Exposure Sources
Personal information is the fuel that drives effective executive phishing.
Knowledge of an executive’s life and network helps attackers create highly targeted executive phishing campaigns.
Executive data removal from common information exposure sources, particularly data brokers, makes cyber criminals’ jobs harder and can reduce the risk that phishing attacks create for executives.
- Employees, Executives, and Board Members complete a quick signup
- DeleteMe scans for exposed personal information
Opt-out and removal requests begin - Initial privacy report shared and ongoing reporting initiated
- DeleteMe provides continuous privacy protection and service all year
DeleteMe is built for organizations that want to decrease their risk from vulnerabilities ranging from executive threats to cybersecurity risks.
news?

Is employee personal data creating risk for your business?


















