Why Data Broker Opt-Outs Are Key to Executive Cybersecurity
DeleteMe
Reading time: 6 minutes

Table of Contents
Executive cybersecurity protection programs need to include a data broker removal process.
This is because, with more modern attacks relying on personal information to succeed, data broker profiles are the go-to source for threat actors looking to customize their campaigns.
Data brokers are companies that sell people’s personal information for a small fee. Their customers are mostly marketers who want to better tailor their ads. However, there is little to prevent cybercriminals from accessing personal information on data brokers as well.
Learn more: The ultimate guide to executive privacy and executive security online
Data broker profiles pose a threat to executive cybersecurity because they:
- Are easy to find with a quick Google search and are among the first few results shown.
- Include a lot of personal information, like names, phone numbers, email addresses, and employment history. The data available on these profiles is only getting more detailed and is being pulled from sources as varied as public records, social media accounts, and breached datasets from the dark web.
- Are cheap or even completely free to access.
Removing executive information from data broker sources is an important part of executive protection. It is also a simple step organizations can take to minimize the risk that their executives will fall victim to a cyber attack.
The Role of Data Brokers In 3 Common Executive Cyber Attacks
Spear phishing, CEO fraud, and account takeover are three common security risks executives face. Here’s the role data brokers play in each.
Spear phishing
What: Spear phishing is a targeted attack in which cybercriminals pose as a known or trusted sender to get the victim to share sensitive information or download malware (for example, ransomware).
How: Like most social engineering attacks, spear phishing typically involves four steps:
- Information gathering
- Relationship development
- Exploitation
- Execution.
The information-gathering step is one of the most important.
Learn more: How cybercriminals use open source intelligence for social engineering
Here, hackers determine who to attack and who their target is likely to share information with, and under what pretext.
Role of data brokers: Data brokers make reconnaissance easier for threat actors.
Rather than looking up a target on LinkedIn, researching them via public records, seeing if there’s any information about them on the corporate site, etc., cybercriminals can simply find all the data they need on a data broker profile.
Here’s the kind of information data brokers have on individuals:
Attackers can then use this information to customize their email/text/social media spear phishing campaigns.
Information hosted on a data broker site can be used to make a spear phishing campaign look like it comes from a friend, colleague, or other third parties an executive is familiar with.
CEO fraud
What: CEO fraud is a type of impersonation scam where threat actors pretend to be senior executives or board members to other business leaders, VIPS, or employees.
Cybercriminals’ aim with CEO fraud is usually to get the recipient to make an unauthorized financial transfer. Sometimes they’ll attempt to con the recipient into disclosing sensitive data or downloading malicious files instead.
How: CEO fraud happens like any other social engineering attack, with the likelihood of success depending heavily on the reconnaissance stage.
However, unlike spear phishing attacks, where criminals can impersonate professional and personal contacts, CEO fraud emails tend to come from C-suite executives, like the CEO or CISO.
Learn more: Data broker opt-outs for CEO fraud prevention
For this reason, it is crucial for threat actors to understand the org chart of their target company.
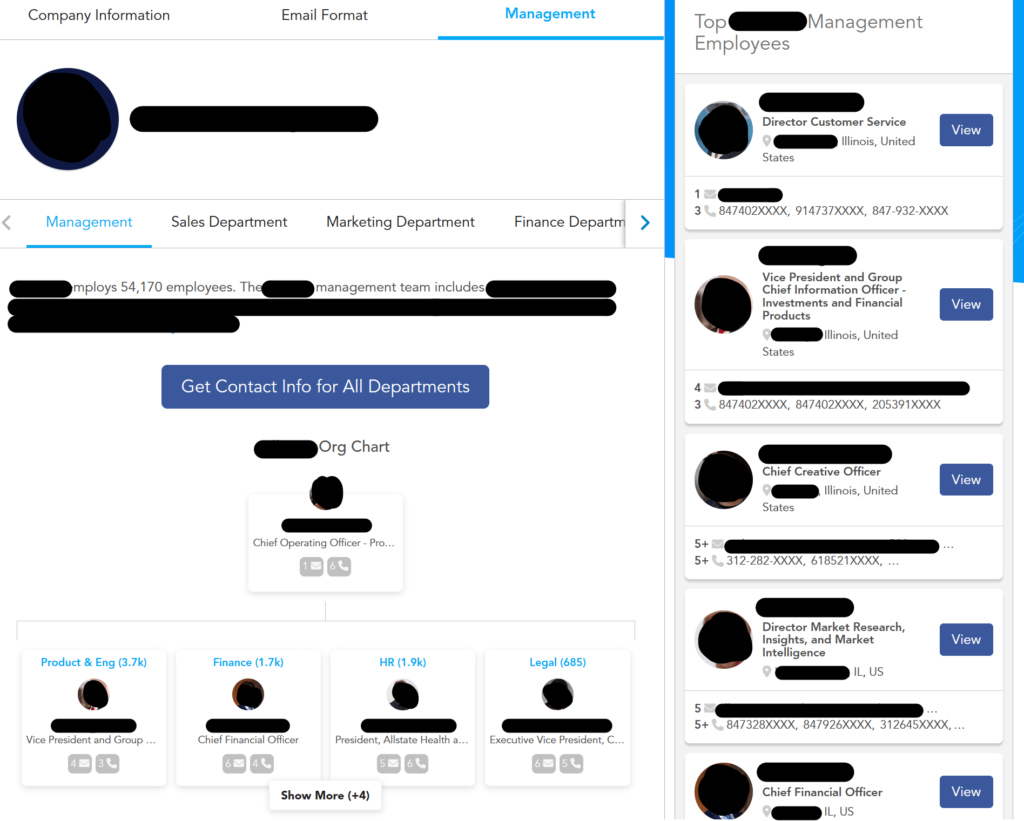
Role of data brokers: In addition to using data brokers to learn more about their targets, cybercriminals can also use them to figure out what the org chart looks like and who their target answers to/has authority over.
Here’s what the org chart looks like for a specific company—as provided by a data broker site.
Account takeover
What: Account takeover is an attack where threat actors take ownership of executive online accounts.
How: Rather than relying solely on data breaches, cybercriminals also use personal information available on the internet to guess passwords, especially for high-value and high-profile targets like corporate executives.
This approach often pays off.
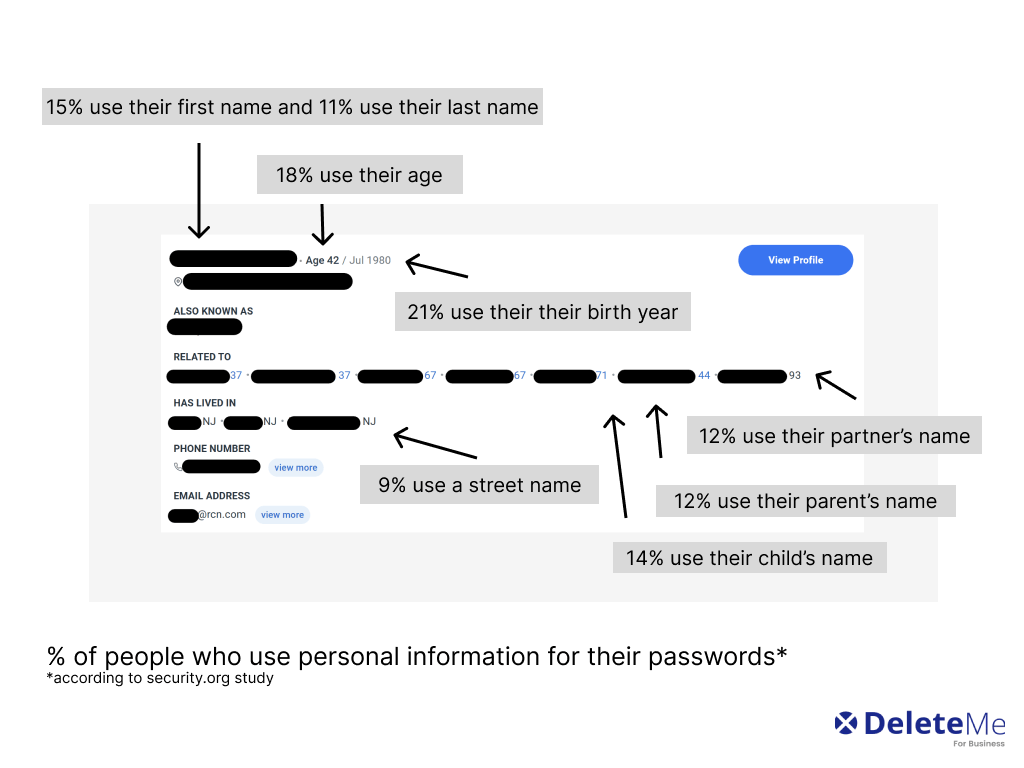
The reason why is that many people use personal information, like the name of their family member or the city they were born in, for their credentials. For example, nearly 25% of executives use their birthday in their password.
Role of data brokers: The personal data people use for credentials is accessible via data brokers.
Here’s an example of how a data broker profile might reveal someone’s password.
Status Quo Is Not Good Enough
Executive security protection typically consists of two elements:
- Executive security training.
- Technical controls.
However, busy executives don’t always have the time to attend security awareness training sessions.
And even when they do, research shows that security training is quickly forgotten unless it happens continuously. According to the nonprofit USENIX, six months after a phishing training session, individuals show no marked improvement in being able to distinguish between a legitimate and a phishing email.
Technical controls meant to catch and remediate cyber risk in real-time similarly can’t be relied on.
Phishing emails that don’t contain malicious links or files can circumvent email security filters; “multi-factor authentication fatigue attacks,” where cybercriminals flood a target’s app with push notifications, can trick executives into authenticating fraudulent login attempts; threats use obfuscation techniques to bypass antivirus and endpoint protection services and tools.
Digital risk protection requires another layer of defense.
Executive Cybersecurity Protection with DeleteMe
Data brokers are an important reconnaissance tool for threat actors and one of the reasons why personalized attacks have become so frequent.
Monitoring for and removing executive personal information from data broker sources won’t completely isolate business leaders from cyber threats. However, doing so will make it harder for cybercriminals to conduct open-source intelligence and will reduce the number of opportunities for exploitation.
- Employees, Executives, and Board Members complete a quick signup
- DeleteMe scans for exposed personal information
Opt-out and removal requests begin - Initial privacy report shared and ongoing reporting initiated
- DeleteMe provides continuous privacy protection and service all year
DeleteMe is built for organizations that want to decrease their risk from vulnerabilities ranging from executive threats to cybersecurity risks.
Want more privacy
news?

Is employee personal data creating risk for your business?

















