3 Ways Data Brokers Enable Corporate Account Takeover
Table of Contents
Corporate account takeover (CATO) is a type of fraud where cybercriminals gain unauthorized access to business accounts such as corporate bank accounts and email accounts.
It is becoming worryingly common. For example, one in five companies had their Microsoft 365 account compromised in 2021.
C-level executives are the most popular target of corporate account takeover, with CEOs and CFOs twice as likely to experience account takeover compared to the general workforce.
Corporate account takeover happens when threat actors are able to acquire employees’ usernames and passwords.
There are many ways this can happen. Breached data sets for sale on the dark web, malware, password spraying, credential stuffing, and phishing campaigns are some of them.
Common advice to protect against account takeover attacks includes using strong passwords, putting in place multi-factor authentication, and screening for compromised credentials.
Another important corporate account takeover risk reduction tactic is data broker removals.
Data brokers are companies that sell people’s personal information online. Thanks to data brokers, executive data points like names, email addresses, dates of birth, pet names, family details, etc., are available with a simple Google search.
This personal data on data broker sites makes it easier for cybercriminals to gain control over corporate accounts. Here’s how.
3 Ways Data Brokers Enable Corporate Account Takeover
Here are three ways data broker profiles increase executives’ risk of account takeover attacks.
Data brokers expose executives’ email addresses, making the first step of password spraying easier
Password spraying is a common account takeover technique involving threat actors “spraying” common passwords across an entire company.
Password spraying attacks start with attackers obtaining username accounts (i.e., email addresses) for a target company. These are typically not hard to find.
Cybercriminals can purchase executive email lists on the dark web, find them on corporate websites, or even guess them (most companies use the same format for emails, for example, firstname.lastname@company.com).
Threat actors can also get usernames through data broker sites.
Here’s what one data broker site offers its customers:
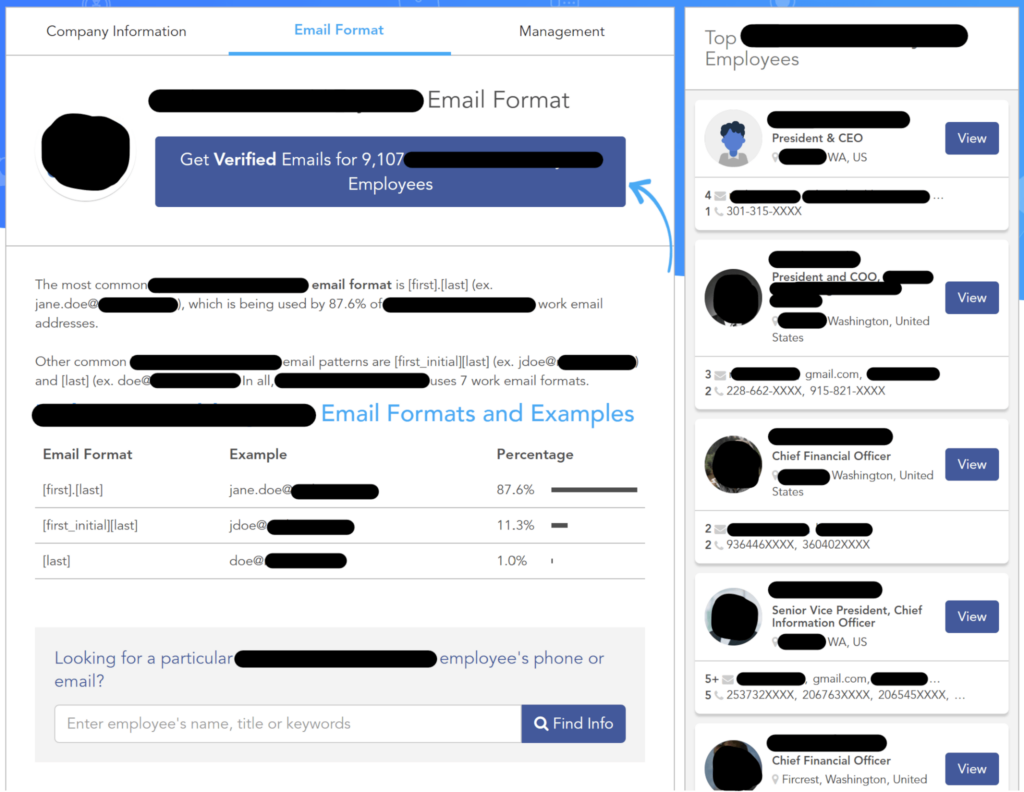
Note how the data broker provides both the most likely email formats used at this company and actual employee email addresses.
Learn more: The Ultimate Guide to Executive Privacy and Executive Security
Once cybercriminals have a company’s employees’ usernames, they can try commonly used passwords to gain access to their accounts. Studies show that high-ranking business executives continue to use passwords like “123456” and “qwerty.”
Data brokers reveal executive personal information, making it more likely they’ll fall for a phishing scam
Social engineering or phishing campaigns are another way for attackers to get corporate passwords.
Cybercriminals use phishing emails, social media messages, texts, or phone calls to trick executives into handing over their account information or downloading spyware.
Threat actors can find executives’ contact details via public records, corporate sites, social media accounts, and data brokers.
The advantage of data brokers is that they provide multiple contact options for every individual, i.e., email addresses, phone numbers, and social media handles:
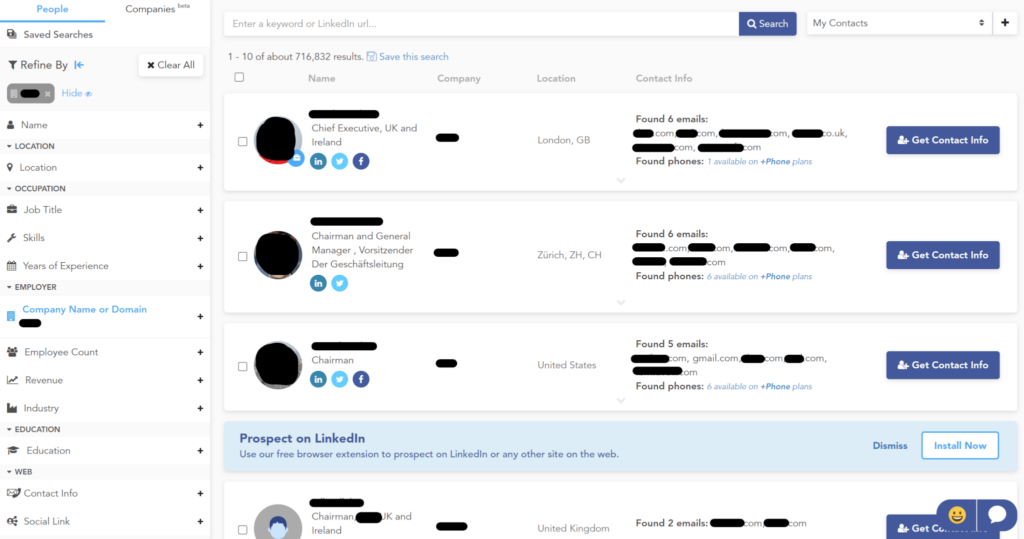
If cyber thieves can personalize their messages to their target, then it’s even more likely that executives will share their login details. This is known as spear phishing. Last year, more than three-quarters of phishing threats detected by SlashNext were spear phishing credential harvesting attacks.
When phishing executives for credentials, bad actors often pretend to be popular companies (Amazon, Microsoft, etc.), social networking sites, financial institutions, Better Business Bureau, or the Federal Trade Commission.
For instance, recently, cybercriminals sent executives in multiple industries phishing emails that looked like they were from DocuSign with the aim of stealing their login details.
Learn more: Data Broker Opt-Outs for CEO Fraud Prevention
Because data brokers compile data from multiple sources, they cut down significantly on the amount of time cybercriminals have to spend on reconnaissance.
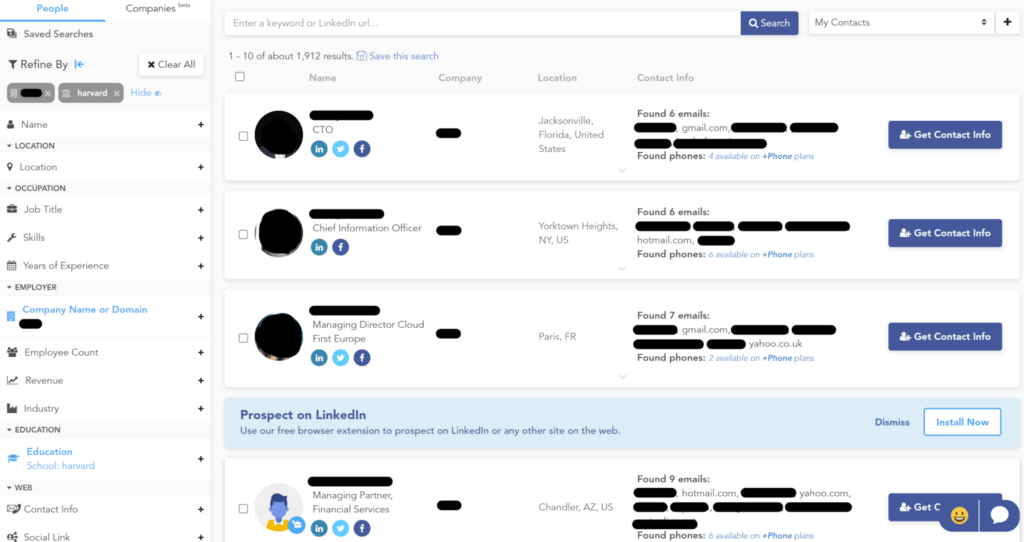
Using the same data broker example as above, notice the filtering options available. Data broker customers can filter employees by their major, school they attended, job title, years of experience, and more.
Now imagine that a threat actor filters employees by:
- Company
- School they attended.
If an executive that attended Harvard gets an email that seems like it comes from the institution or fellow alumni, they are immediately more likely to click on a phishing link within the email.
Data brokers disclose information individuals use for passwords, making credential-stuffing attacks more likely to succeed
Credential stuffing is generally defined as an attack where threat actors use breached details to log into other accounts.
However, for high-value targets, threat actors also use personal information. The reason why is that many people use sensitive information for their login credentials.
Popular password components include birth year (21%), pet’s name (18%), child’s name (14%), parent’s name (12%), partner’s name (12%), street name (9%), and graduation year (7%).
All this information is easy to find online. Most of it is also available on data broker sources.
Learn more: The Link Between Weak Passwords, Data Breaches, and Data Brokers
For instance, here’s a data broker that discloses an individual’s address history and family details:
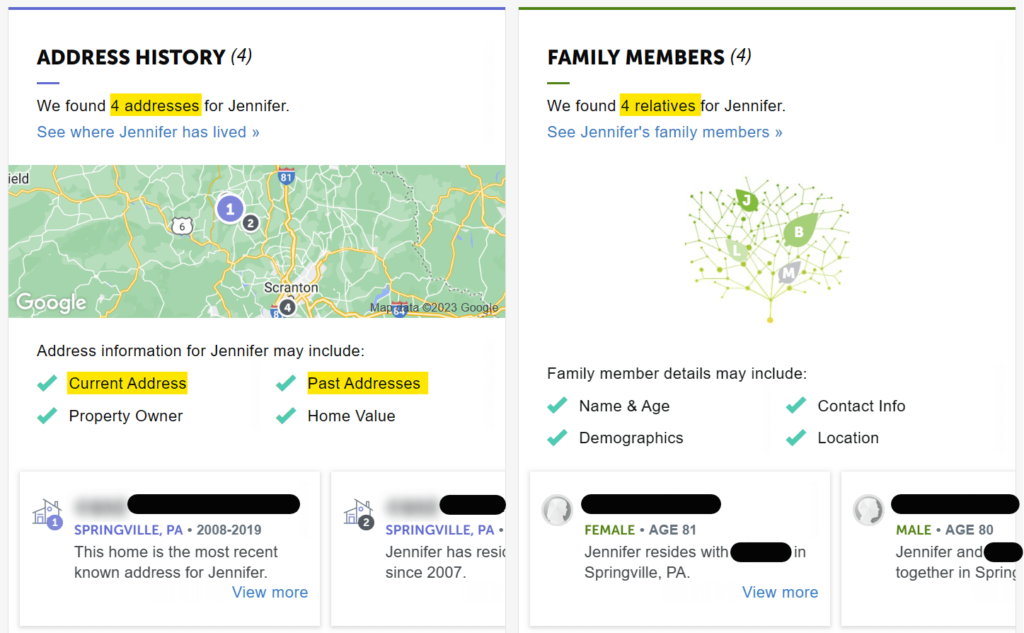
If this person used their street name or parent’s/partner’s/child’s name for their password, bad actors would be able to break into their accounts.
Cybercriminals don’t even have to “stuff” this data manually. Instead, they can automate the process with advanced tools that let them enter personal data about their target (for example, names of family members or pets) and generate potential passwords from that data.
Because hackers increasingly use sophisticated bots to obfuscate their activities, it’s very difficult for cybersecurity teams to detect these kinds of attacks.
Data Broker Removal vs. Corporate Account Takeover Attacks
Easy access to executive personal information online makes it easier for threat actors to carry out account takeover attacks.
Removing executive profiles from data brokers makes it harder for threat actors to gather executive personal information. This, in turn, will make it more likely that attackers will move to a different target.
Who Is At Risk of Corporate Account Takeover?
High-level executives are at a particularly high risk of account takeover.
However, executive assistants are also targeted. This is mainly because they have access to executive calendars and accounts and because they sometimes also control the executive’s inbox.
HR and accounting/financial teams are also targeted disproportionately compared to the average employee.
Other Steps Organizations Can Take to Protect Against Corporate Account Takeover
In addition to opting out of data broker sources, organizations should also take the following precautions to protect against account takeover:
- Install and maintain security safeguards like antivirus on all workstations and devices.
- Teach employees to keep an eye out for suspicious account activity, like changed settings or unauthorized transactions (ACH transactions, wire transfers, etc.) on online banking accounts.
- Provide training on how to recognize suspicious emails, texts, social media messages, and malware-infected websites.
- Implement strong multi-factor authentication, like hardware MFA keys. Cybercriminals can circumvent call and SMS-based MFA solutions with phishing emails and texts or via SIM swap scams (where scammers impersonate their target to their phone company to get them to port over their target’s phone number to their own).
- Put in place strong password policies and give executives and employees access to password managers.
- Stop relying on security questions for account security. Answers to security questions like “what was the name of your first pet?” or “what is your mother’s maiden name?” are available via public records and data broker sources.
- Educate employees about the risks of oversharing on the internet and teach them how to reduce their digital footprint.
How DeleteMe Minimizes the Risk of Corporate Account Takeover
DeleteMe removes executive and employee personal information from some of the most popular data broker sites. Often, information from these sites appears on the first page of Google when someone searches for a person’s email, phone number, or other personal information.
Because many corporate account takeover techniques rely on hackers being able to find and exploit executive details, making this data as difficult to find as possible is a critical step in corporate account takeover prevention.
- Employees, Executives, and Board Members complete a quick signup
- DeleteMe scans for exposed personal information
- Opt-out and removal requests begin
- Initial privacy report shared and ongoing reporting initiated
- DeleteMe provides continuous privacy protection and service all year
DeleteMe is built for organizations that want to decrease their risk from vulnerabilities ranging from executive threats to cybersecurity risks.












