How Cybercriminals Use Data Brokers for Executive Phishing
Table of Contents
Without question, executive phishing is one of the biggest threats to your organization.
Despite growing awareness around phishing, it remains a top infection vector, and executives are some of the most common victims. A recent report by Ivanti shows that executives (CEOs, CFOs, etc.) are four times more likely to fall for a phishing scam than the average employee.
It’s not that business leaders are more gullible. What makes executive phishing attacks so dangerous is that they are more often than not personalized to their target (i.e., “spear phishing”). This means executive phishing is more convincing and harder to spot.
There are many ways for hackers to get an executive’s personal information. Data brokers are one of the easiest. These are companies that collect people’s personal information from a variety of sources (like social media, public records, apps, etc.), pull this data into one profile, and sell it to anyone who wants it.
Here’s how data brokers facilitate executive phishing. Plus, steps you can take to protect business leaders.
How Data Brokers Make Executive Phishing Easier
Executive phishing involves three steps: finding a high-profile target, researching the target, and creating the bait. Here’s the role data brokers play.
Finding a high-profile target
Like any other spear phishing attack, executive phishing attacks start with cybercriminals finding specific individuals to phish.
How does this happen? Well, thanks to a series of document leaks from a prominent cybercriminal group, we know that threat actors use business data brokers to find potential targets’ names, job roles, and contact information (email addresses, phone numbers, etc.).
These kinds of business data brokers are valuable because they provide lists of employees, including C-suite ones, for thousands of companies worldwide.
Learn more: The ultimate guide to executive privacy and executive security online
On many business data brokers, it’s even possible to filter employees by department, seniority, and job title:
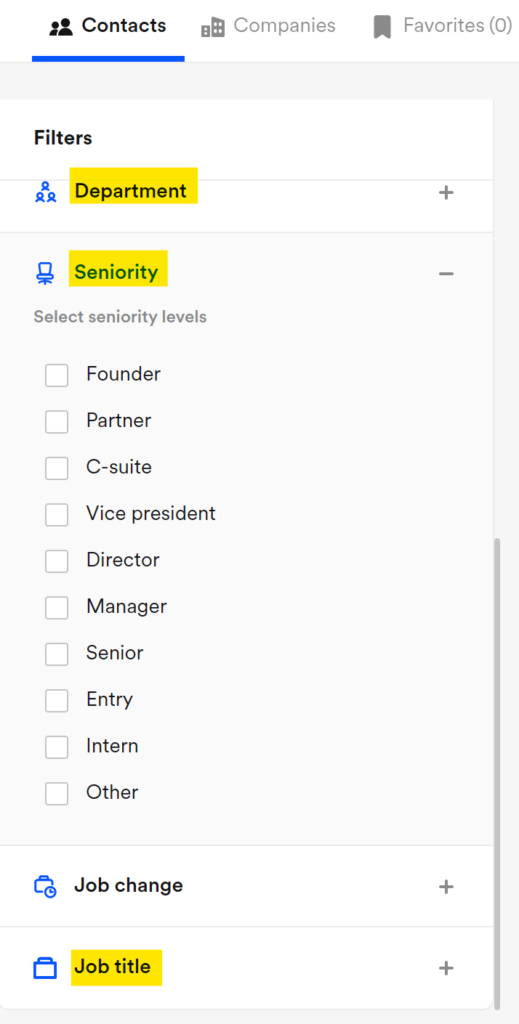
Researching the target
Once attackers identify a target, they start their research. Here’s the kind of information they can find on data broker databases:
Work experience and education
The profiles that business data brokers have on executives include a ton of exploitable information, like their work experience and education.
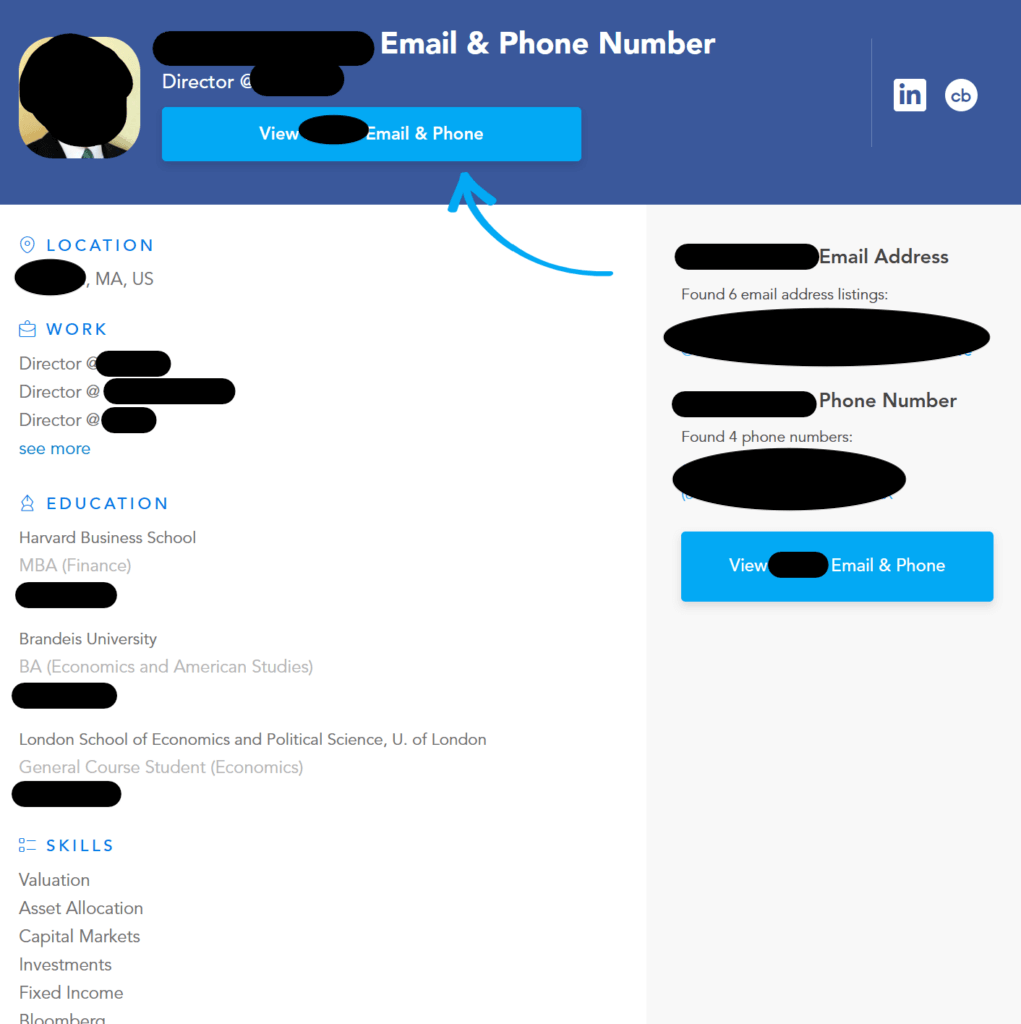
Knowing where an executive went to school and where they worked previously can help threat actors find a “hook” for executive phishing campaigns.
Business org chart
Some business data brokers also show org charts for companies and employees, including for specific departments:
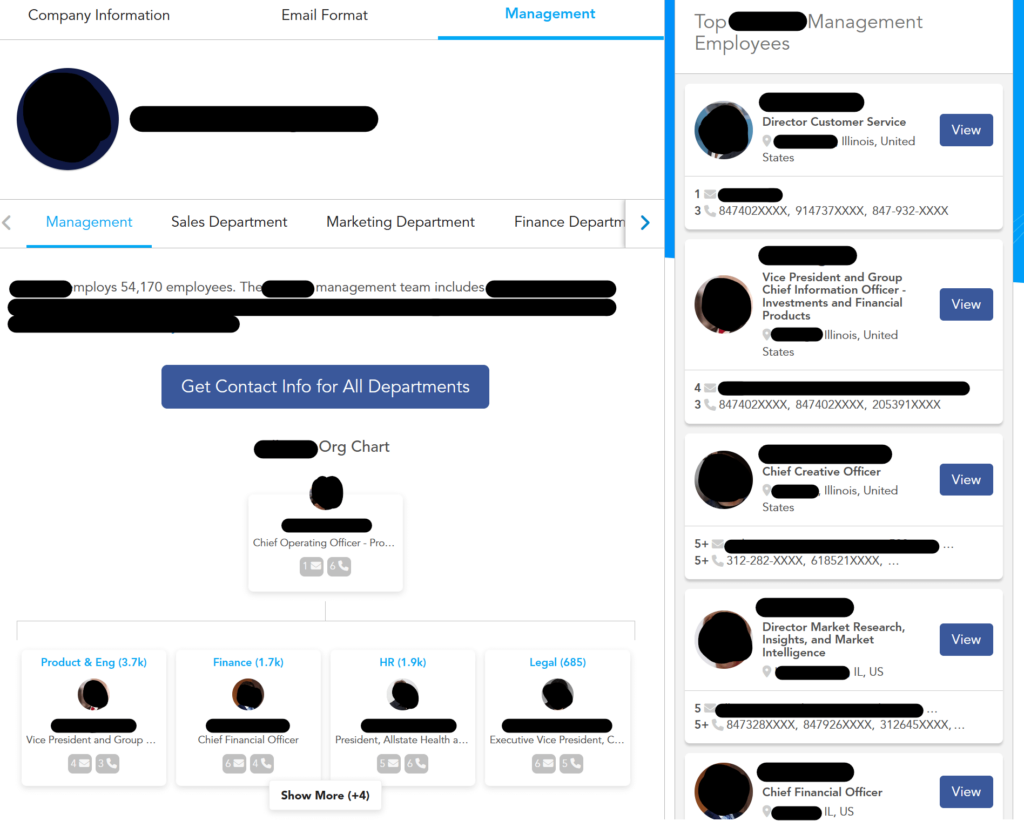
Why does this matter?
For an executive phishing attack to succeed, there needs to be a justifiable and valid context between the sender and the recipient.
Learn more: Data broker opt-outs for CEO fraud prevention
For this reason, executive phishing attacks that target C-level executives often seem like they come from other high-level employees. Knowing a company’s internal structure makes it easier for scammers to choose the right individuals to impersonate.
Family members
Cybercriminals are not limited to professional data when it comes to information gathering.
In addition to business data brokers, there are also “regular” data brokers, commonly known as people search sites. These data brokers have more sensitive data about individuals, including details about their family members and marital status.
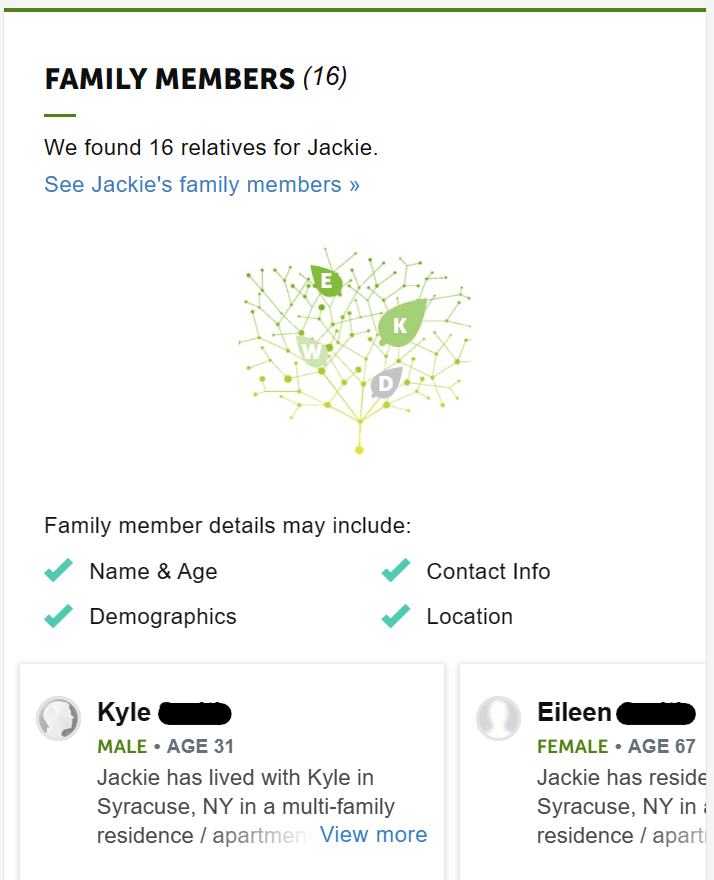
Depending on the context of the phishing email, it might make sense for cybercriminals to include this information as proof that they are trustworthy.
Social profiles
Some data brokers also include links to people’s professional and personal social media profiles like LinkedIn, Facebook, Instagram, etc.
Based on the kind of information executives share on their social accounts, this could give cybercriminals even more data to play with. For example, their posts and comments can give attackers an indication of the executive’s tone of voice.
Threat actors can then match the language in their email to the language the executive likely uses. Today, they don’t even have to do this manually. Instead, they can provide a sample of an executive’s communications to AI chatbots to create a message in their writing style, saving time and cutting down on potential mistakes.
Creating the bait
When a threat actor gathers enough personal information about their target, they can use social engineering tactics to create a convincing executive phishing campaign. This can come in the form of a phishing email, phone call, or social media/text message.
Whatever a cybercriminal’s goal—tricking the executive into handing over sensitive data (login credentials, bank account or credit card details, etc.), deploying malware (for example, ransomware), or authorizing a fraudulent wire transfer—they are likely to succeed. That is, as long as they have thoroughly researched their target and picked a trusted person to imitate. More than one in three business leaders say they have clicked on a phishing link.
Data Broker Removal Is Crucial for Executive Phishing Prevention
Data broker removal makes cyber criminals’ jobs harder and can reduce the risk phishing attacks create for executives.
This is because the information listed on data brokers saves threat actors a ton of time. Rather than having to piece bits of information from various different sources themselves (social media, public records, past data breaches, etc.), they can get it all in one place.
Unfortunately, the role that data brokers play in executive phishing attacks (and cybersecurity threats in general) is rarely talked about.
To minimize executive phishing threats, it’s more common to recommend security awareness training, email phishing protection solutions, and multi-factor authentication (MFA).
While relevant and necessary, these controls can’t stop personalized attacks. Data broker removal services can.
- Employees, Executives, and Board Members complete a quick signup
- DeleteMe scans for exposed personal information
- Opt-out and removal requests begin
- Initial privacy report shared and ongoing reporting initiated
- DeleteMe provides continuous privacy protection and service all year
DeleteMe is built for organizations that want to decrease their risk from vulnerabilities ranging from executive threats to cybersecurity risks.












